http://openvpn.net/index.php/download/access-server-downloads.html
OpenVPN Access Server is a full featured SSL VPN software solution that
integrates OpenVPN server capabilities, enterprise management
capabilities, simplified OpenVPN Connect UI, and OpenVPN Client software
packages that accommodate Windows, MAC, and Linux OS environments.
OpenVPN Access Server supports a wide range of configurations,
including secure and granular remote access to internal network and/ or
private cloud network resources and applications with fine-grained
access control.
http://openvpn.net/index.php/download/community-downloads.html
=============================
http://openvpn.net/index.php/access-server/download-openvpn-as-vm/202.html?osfamily=Virtual%20Appliance%20Windows%20%28VHD%29&ex=1
Using the OpenVPN Access Server Windows (VHD) Virtualization Version
[It uses Ubuntu]
Virtual Appliance Windows (VHD) Version of OpenVPN Access Server to Begin Downloading
Using the OpenVPN Access Server Virtual Appliance For Windows (VHD) Virtualization Version
Release with Access Server v1.8.4
Initial Setup of Access Server The first time the virtual appliance boots, you will be queried for
some information. First, you must agree to the End User License
Agreement (EULA). Next, you will be asked to enter some basic settings
that the OpenVPN Access Server needs to initialize itself. These
settings may be safely defaulted by pressing 'Enter'.
At the end of the boot sequence, the appliance window will turn to a blue background and show the URL of the
appliance management interface.
Enter this URL into a browser to continue the setup. You will likely
receive a browser warning about the web server SSL certificate not being
recognized. You can safely ignore these warnings.
On the appliance management interface, enter the username and password for the appliance. The initial credentials are:
Username: root
Password: openvpnas
See the
Virtual Appliance section of the FAQ for information on how to change the root password.
The
Admin Account for OpenVPN-AS needs to be setup through terminal by doing the following:
Change the password:
passwd openvpn
You will then be prompted to set a password for the user openvpn,
after setting the password you can login to the Admin UI with the
Username openvpn and the password you set.
Once logged in, you
will be directed to the "System Information" page which gives you basic
control over the virtual appliance. You can reboot, shut down, or change
the network settings of the appliance.
Note:Keep in mind that
the appliance will acquire its own IP address from DHCP that is separate
from the IP address of the VMware host machine. You can use this
DHCP-assigned address, or enter a fixed IP address under the "Network"
tab.
The next step is to log into the OpenVPN Access Server Admin Web UI.
On the "System Information" page, click on the "AS Admin Login" link
located in the upper right corner of the page. You will receive another
certificate-related browser warning at this point; that warning can also
be ignored. At the Access Server Admin Web UI login page, enter the
same username and password you entered previously for the appliance
management interface.
Once logged in to the Access Server Admin
Web UI, follow the instructions in the "Welcome to the Access Server
Admin UI" information box to complete configuration of the Access
Server.
=============================
OpenVPN: Manual para GNU/Linux y Windows 7 32bits y 64bits. Cliente/Servidor. SSL/TLS
OpenVPN es un cliente/servidor VPN tanto para equipos GNU/Linux como para Windows.
¿Para qué sirve hacer esto?
Para conectarnos a internet de una
manera segura desde cualquier red ya sea cableada o WiFi, con cifrado WEP/WPA o sin cifrar. Todo el tráfico irá c
ifrado a través de un Túnel
desde el AP que nos conectamos hasta nuestra casa y desde allí saldrá a
internet, es como estar en nuestra casa. Lo malo es que debes tener una
buena velocidad de subida, ya que de eso dependerá en mayor medida tu
velocidad de bajada (a no ser que la red donde te conectes tenga menos
bajada que la velocidad de subida de tu conexión).
También sirve en caso de no redigirir el tráfico, para poder acceder a
los recursos compartidos de nuestra casa como puede ser imprimir desde
la Universidad, copiarnos archivos desde el disco duro compartido de
casa etc.
La VPN será SSL/TLS, y podemos encontrar dos tipos, TUN y TAP.
TUN: El controlador
TUN emula un dispositivo punto a punto, es utilizado para crear
túneles virtuales operando con el protocolo IP.
De esta forma se puede encapsular todos los paquetes que se transporten
a través de él como datagramas TCP o UDP (más adelante veréis que
escogemos UDP en lugar de TCP, y preguntaréis que por qué ya que TCP es
conectivo, fiable y Orientado a conexión). Las máquinas que queden
detrás de cada uno de los extremos del enlace pertenecerán a subredes
diferentes.
TAP: Simula una interfaz de red Ethernet, más comúnmente conocido como modo puente o bridge, estos túneles virtuales
encapsulan directamente paquetes ethernet.
Esta situación permite empaquetar entramados diferentes al IP. Las
máquinas situadas detrás de cada uno de los extremos del enlace pueden
operar como parte de la misma subred (si se utiliza el protocolo IP). El
modo de funcionamiento puente es particularmente útil para enlazar
usuarios remotos, ya que éstos pueden conectarse a un mismo servidor y
virtualmente formar parte de la red principal.
En el manual
usaremos TUN.
En este manual os voy a explicar cómo hacerlo en
GNU/Linux, aunque en esencia, es lo mismo para
Windows, únicamente cambian los comandos en la consola (cmd.exe),
los certificados y las llaves, son los mismos para los dos, es decir, puedes crear TODO en
GNU/Linux y luego pasarlo a
Windows para usarlo (ya sea cliente o servidor), únicamente deberás cambiar la extensión del
cliente/servidor .conf por .ovpn
Voy a explicaros como realizar la configuración más segura posible.
- Usaremos una llave
RSA para crear CA.key de 2048bits sin afectar lo más mínimo al rendimiento de la VPN.
- La
llave simétrica será AES-256bits-CBC
(Encadenamiento de Cifrado en Bloque) uno de los más seguros (OpenVPN
incluye todo esto, no hay que “programarlo” ni nada parecido).
- Incluiremos
TLS/AUTH una firma HMAC adicional para todos las negociaciones SSL/TLS para la verificación de la integridad. Cualquier paquete
UDP que no posea la firma HMAC correcta es bloqueado. La firma
HMAC TLS-AUTH provee un nivel de seguridad adicional mas allá del que provee
SSL/TLS,
de esta forma nos protegemos de ataques DoS, escaneo de puertos y le
ahorramos trabajo al servidor (porque si esto falla al intentar la
autenticación lo corta y no lo sigue intentando).
-
Protocolo UDP en lugar de TCP porque es más fuerte
frente a ataques DoS y escaneos de puertos (UDP es no conectivo, no
fiable, no orientado a conexión).
GNU/Linux Ubuntu
Instalamos Openvpn con el siguiente comando desde los repositorios:
sudo apt-get install openvpn
Ahora vamos a copiar los archivos easy-rsa y sample-config-files a
/etc/openvpn/ (previamente hemos ido al directorio con la orden cd).
ubuntu@ubuntu:/usr/share/doc/openvpn/examples$ ls
easy-rsa sample-config-files sample-keys sample-scripts
Copiamos easy-rsa y sample-config-files a /etc/openvpn/
ubuntu@ubuntu:/usr/share/doc/openvpn/examples$ sudo cp -R easy-rsa/ /etc/openvpn/
ubuntu@ubuntu:/usr/share/doc/openvpn/examples$ sudo cp -R sample-config-files/ /etc/openvpn/
Ahora nos metemos en el directorio de trabajo y veremos muchos ficheros:
ubuntu@ubuntu:/etc/openvpn/easy-rsa/2.0$ ls
build-ca build-key-server Makefile sign-req
build-dh build-req openssl-0.9.6.cnf.gz vars
build-inter build-req-pass openssl.cnf whichopensslcnf
build-key clean-all pkitool
build-key-pass inherit-inter README.gz
build-key-pkcs12 list-crl revoke-full
Ejecutamos el siguiente comando para crear una carpeta en este directorio donde almacenaremos las claves:
mkdir keys
Es en este directorio donde se almacenaran las llaves privadas
(.key), los archivos de requerimiento de certificado (.csr) y los
certificados (.crt) y otros archivos.
- Las llaves .key son PRIVADAS, han de ser copiadas por un medio seguro.
- Los certificados .crt y el requerimiento .csr puede pasarse sobre un medio inseguro (emails, messenger).
Generar la llave y el certificado para la Autoridad Certificadora (CA).
En esta parte vamos a crear los certificados y las llaves para la CA,
para el servidor y para el cliente, nos logueamos en la consola como
root (siempre como root para dejarnos de líos).
Ahora vamos a editar el archivo “vars”.
Nos situamos en el directorio de trabajo:
cd /etc/openvpn/easy-rsa/2.0/
gedit vars
- Ahora modificamos KEY_COUNTRY, KEY_PROVINCE, KEY_CITY, KEY_ORG y KEY_MAIL a vuestro gusto, pero no podéis dejarlo en blanco.
- También modificamos la ruta donde están las KEYS, ya que luego haremos un ./clean-all y si no está la ruta correcta, dará error.
- El tamaño de la llave RSA es controlado por la variable KEY_SIZE en el archivo vars, por tanto en lugar de tener 1024 (bits), ponemos 2048 (bits) si queréis más seguridad (recomiendo 2048).
Una vez lo hayáis modificado, guardamos y salimos, os debería quedar algo así:
# easy-rsa parameter settings
# NOTE: If you installed from an RPM,
# don’t edit this file in place in
# /usr/share/openvpn/easy-rsa –
# instead, you should copy the whole
# easy-rsa directory to another location
# (such as /etc/openvpn) so that your
# edits will not be wiped out by a future
# OpenVPN package upgrade.
# This variable should point to
# the top level of the easy-rsa
# tree.
export EASY_RSA=”`pwd`”
#
# This variable should point to
# the requested executables
#
export OPENSSL=”openssl”
export PKCS11TOOL=”pkcs11-tool”
export GREP=”grep”
# This variable should point to
# the openssl.cnf file included
# with easy-rsa.
export KEY_CONFIG=`$EASY_RSA/whichopensslcnf $EASY_RSA’
# Edit this variable to point to
# your soon-to-be-created key
# directory.
#
# WARNING: clean-all will do
# a rm -rf on this directory
# so make sure you define
# it correctly!
export KEY_DIR=”/etc/openvpn/easy-rsa/2.0/keys/”
# Issue rm -rf warning
echo NOTE: If you run ./clean-all, I will be doing a rm -rf on $KEY_DIR
# PKCS11 fixes
export PKCS11_MODULE_PATH=”dummy”
export PKCS11_PIN=”dummy”
# Increase this to 2048 if you
# are paranoid. This will slow
# down TLS negotiation performance
# as well as the one-time DH parms
# generation process.
export KEY_SIZE=2048
# In how many days should the root CA key expire?
export CA_EXPIRE=3650
# In how many days should certificates expire?
export KEY_EXPIRE=3650
# These are the default values for fields
# which will be placed in the certificate.
# Don’t leave any of these fields blank.
export KEY_COUNTRY=”XXXX”
export KEY_PROVINCE=”XXX”
export KEY_CITY=”XXXX”
export KEY_ORG=”XXXXX”
export KEY_EMAIL=”XXXXX@XXX.com”
En el mismo directorio tecleamos lo siguiente para limpiar todos los archivos que haya en /keys/.
source ./vars
./clean-all
Parámetros Diffie Hellman
Vamos a generar estos parámetros necesarios para el servidor.
En consola y en el mismo directorio de siempre (/etc/openvpn/easy-rsa/2.0/)
./build-dh (recuerda ejecutarlo como root)
Os saldrá algo parecido a esto:
root@Portatil:/etc/openvpn/easy-rsa/2.0# ./build-dh
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
……………………………….+……………….++*++*
……………………………….+……………….++*++*
root@Portatil:/etc/openvpn/easy-rsa/2.0#
Nota: los guiones anteriores eran simples guiones, estos que vienen a
continuación y que por ejemplo están antes que initca son dos guiones
juntos, parece que es uno largo pero no.
Creación certificado para la CA
Ahora creamos el certificado para la CA:
./pkitool –initca
Os saldrá algo como esto:
root@Portatil:/etc/openvpn/easy-rsa/2.0# ./pkitool –initca
Using CA Common Name: vpn CA
Generating a 2048 bit RSA private key
…….+++
………….+++
writing new private key to ‘ca.key’
—–
root@Portatil:/etc/openvpn/easy-rsa/2.0#
Generación de certificado y llaves para el SERVER
./pkitool –server servidor
Nos saldrá algo así:
root@Portatil:/etc/openvpn/easy-rsa/2.0# ./pkitool –server servidor
Generating a 2048 bit RSA private key
…………………………+++
…………………………………..+++
writing new private key to ‘servidor.key’
—–
Using configuration from /etc/openvpn/easy-rsa/2.0/openssl.cnf
Check that the request matches the signature
Signature ok
The Subject’s Distinguished Name is as follows
countryName PRINTABLE:’XX’
stateOrProvinceName PRINTABLE:’XXX’
localityName PRINTABLE:’XXX’
organizationName PRINTABLE:’XXXX’
commonName PRINTABLE:’servidor’
emailAddress :IA5STRING:”XXXXXX”
Certificate is to be certified until Jun 19 09:40:27 2020 GMT (3650 days)
Write out database with 1 new entries
Data Base Updated
root@Portatil:/etc/openvpn/easy-rsa/2.0#
Todos los valores los obtiene del archivo VARS, y el Common Name lo obtiene de “servidor” que está a continuación de “–server”.
Generación de certificado y llaves para el CLIENTE
./pkitool cliente1
Nos saldrá algo así:
root@Portatil:/etc/openvpn/easy-rsa/2.0# ./pkitool cliente1
Generating a 2048 bit RSA private key
………………………….+++
………………………………………….+++
writing new private key to ‘cliente1.key’
—–
Using configuration from /etc/openvpn/easy-rsa/2.0/openssl.cnf
Check that the request matches the signature
Signature ok
The Subject’s Distinguished Name is as follows
countryName PRINTABLE:’XX’
stateOrProvinceName PRINTABLE:’XXX’
localityName PRINTABLE:’XXX’
organizationName PRINTABLE:’XXX’
commonName PRINTABLE:’cliente1′
emailAddress :IA5STRING:’XXXX’
Certificate is to be certified until Jun 19 09:41:34 2020 GMT (3650 days)
Write out database with 1 new entries
Data Base Updated
root@Portatil:/etc/openvpn/easy-rsa/2.0#
Para generar más clientes hacemos lo siguiente:
source ./vars
./pkitool cliente2
Si queremos el tercero hacemos:
source ./vars
./pkitool cliente3
Antes de crear cada certificado debemos ejecutar source ./vars (por si queréis más).
Ahora nos vamos a:
cd /etc/openvpn/easy-rsa/2.0/keys/
Y veremos todas las claves (comando ls para verlas).
Generar llave TLS-AUTH
openvpn –genkey –secret ta.key (donde ta.key es la llave que deberemos usar tanto en el servidor como en el cliente).
En la
configuración del servidor (servidor.conf o servidor.ovpn) deberemos poner:
tls-auth ta.key 0 (0 de Incoming)
En la
configuración del cliente (cliente.conf o cliente.ovpn) deberemos poner:
tls-auth ta.key 1 (1 de Outgoing)
A continuación os pongo una tabla de qué es cada cosa.

Podemos agruparlos por carpetas para mayor comodidad siguiendo la
tabla ya que por ejemplo ca.crt tiene que estar en todos los
clientes/servidores (servidor, cliente1, cliente2, etc).
Archivo de Configuración del Cliente (client.conf)
Viene una pequeña guía de para qué sirve cada comando, tenéis que modificar:
- remote my-server-1 1194 ya que aquí deberemos poner el host dyndns que tengáis,
Host en DynDNS para servidores domésticos como FTP, VPN, servidor de juegos o servidor WEB : Manual DynDNS
- ca ca.crt cert client.crt y key client.key lo debéis cambiar por el
nombre que le habéis puesto a cliente, en este caso cliente1, cliente2 y
con la RUTA COMPLETA al archivo para evitarnos problemas, quedaría así:
ca /etc/openvpn/easy-rsa/2.0/keys/ca.crt
cert /etc/openvpn/easy-rsa/2.0/keys/cliente1.crt
key /etc/openvpn/easy-rsa/2.0/keys/cliente1.key
-En el siguiente fragmento veis el TLS-AUTH que usaremos, quitamos e
punto y coma (;) y lo activaremos, el ta.key también ponemos la ruta
completa de la ta.key.
# If a tls-auth key is used on the server
# then every client must also have the key.
tls-auth ta.key 1
- Como hemos elegido un cifrado AES-256-CBC pues lo ponemos:
# Select a cryptographic cipher.
# If the cipher option is used on the server
# then you must also specify it here.
cipher AES-256-CBC
Y ya tenemos el cliente listo.
La ruta completa de cada archivo (ca.crt cliente1.key etc, no hace
falta ponerla siempre y cuando el client.conf esté en la misma carpeta
que ellas, pero para no tener problemas pues ponemos la ruta completa).
Archivo de Configuración del Servidor (server.conf)
- En el servidor debemos poner la IP interna que tendremos en la red
para escuchar, el puerto, si es el de por defecto no habrá que tocarlo.
- Ponemos las rutas completas de los siguientes archivos:
ca ca.crt
cert server.crt
key server.key
- dh dh2048.pem ya que lo hemos puesto de 2048 bits.
- El rango del servidor no hace falta tocarlo, el cifrado que hemos elegido y la TLS-AUTH.
Aquí no he explicado con detalle la configuración del servidor,
porque poca gente va a tener un ordenador con GNU/Linux o Windows
encendido dedicado únicamente a esto, es mucho más cómodo un router con
firmwares de terceros como Tomato y el correspondiente módulo OpenVPN
donde es todo gráfico, a continuación os pongo unas capturas de pantalla
para que lo veáis junto con el LOG del router al arrancar la VPN.
Nota: las claves se meten en las casillas haciendo un gedit ca.crt
(por ejemplo), copiamos y pegamos todo lo que aparece en el gedit y
listo! (sí, todos esos símbolos y letras).
Click en la foto para ampliarla y verla mejor.
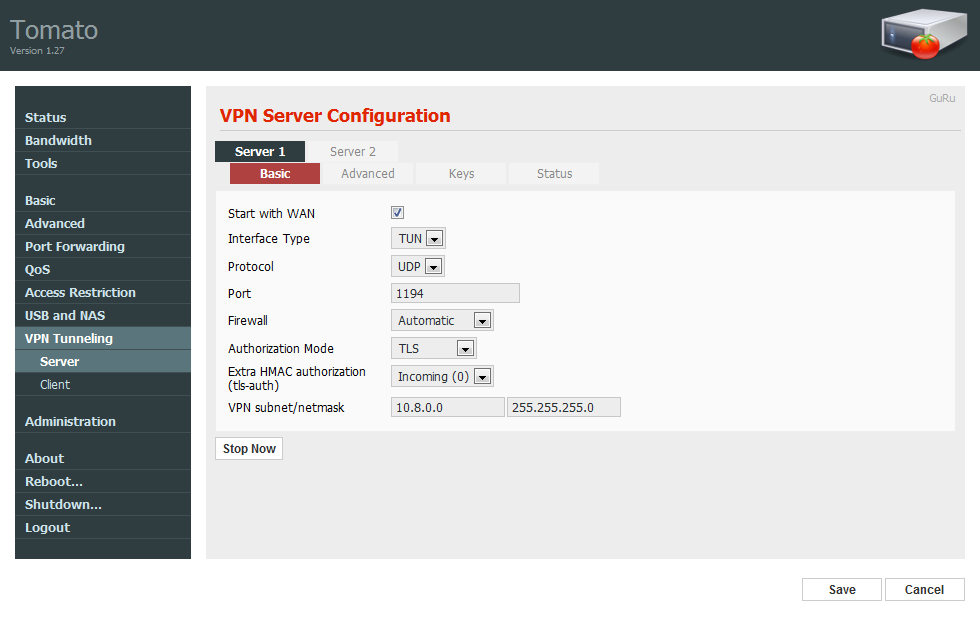
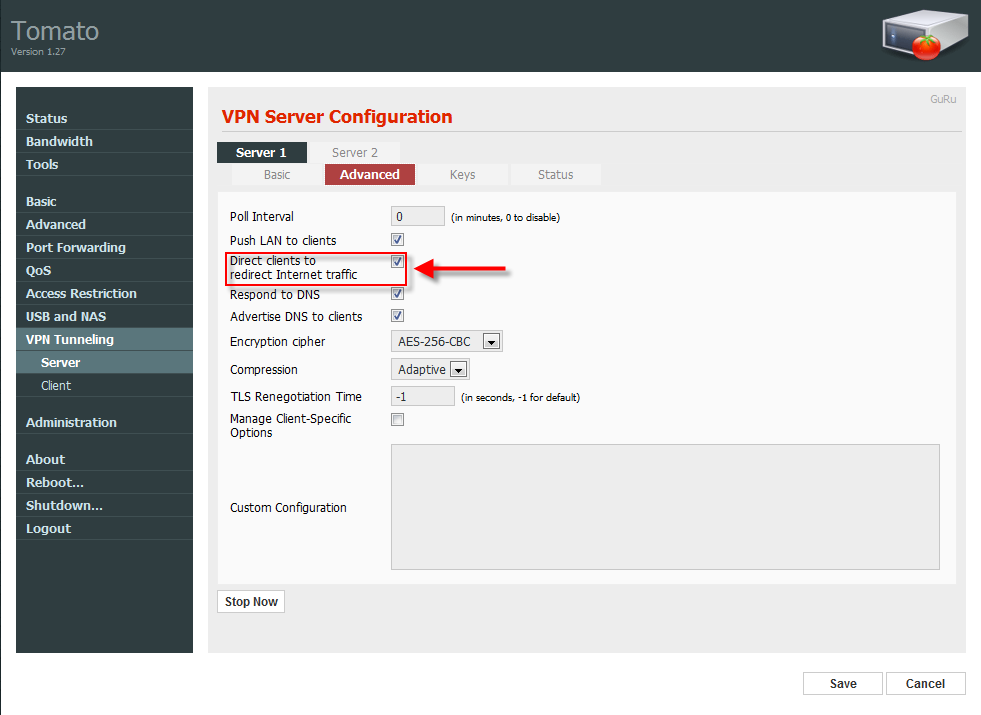

Pruebas de conectividad:
Log de inicio de OpenVPN en el router:
Jun 21 18:14:39 router daemon.notice openvpn[344]: OpenVPN 2.1.1 mipsel-unknown-linux-gnu [SSL] [LZO2] built on Feb 17 2010
Jun 21 18:14:39 router daemon.warn openvpn[344]: NOTE: OpenVPN 2.1
requires ‘–script-security 2′ or higher to call user-defined scripts or
executables
Jun 21 18:14:42 router daemon.notice openvpn[344]: Diffie-Hellman initialized with 2048 bit key
Jun 21 18:14:42 router daemon.notice openvpn[344]: Control Channel
Authentication: using ‘static.key’ as a OpenVPN static key file
Jun 21 18:14:42 router daemon.notice openvpn[344]: Outgoing Control
Channel Authentication: Using 160 bit message hash ‘SHA1′ for HMAC
authentication
Jun 21 18:14:42 router daemon.notice openvpn[344]: Incoming Control
Channel Authentication: Using 160 bit message hash ‘SHA1′ for HMAC
authentication
Jun 21 18:14:42 router daemon.notice openvpn[344]: TLS-Auth MTU parms [ L:1558 D:166 EF:66 EB:0 ET:0 EL:0 ]
Jun 21 18:14:42 router daemon.notice openvpn[344]: TUN/TAP device tun21 opened
Jun 21 18:14:42 router daemon.notice openvpn[344]: TUN/TAP TX queue length set to 100
Jun 21 18:14:42 router daemon.notice openvpn[344]: /sbin/ifconfig tun21 10.8.0.1 pointopoint 10.8.0.2 mtu 1500
Jun 21 18:14:42 router daemon.notice openvpn[344]: /sbin/route add -net 10.8.0.0 netmask 255.255.255.0 gw 10.8.0.2
Jun 21 18:14:42 router daemon.notice openvpn[344]: Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:135 ET:0 EL:0 AF:3/1 ]
Jun 21 18:14:42 router daemon.notice openvpn[407]: Socket Buffers: R=[108544->131072] S=[108544->131072]
Jun 21 18:14:42 router daemon.notice openvpn[407]: UDPv4 link local (bound): [undef]:1194
Jun 21 18:14:42 router daemon.notice openvpn[407]: UDPv4 link remote: [undef]
Jun 21 18:14:42 router daemon.notice openvpn[407]: MULTI: multi_init called, r=256 v=256
Jun 21 18:14:42 router daemon.notice openvpn[407]: IFCONFIG POOL: base=10.8.0.4 size=62
Jun 21 18:14:42 router daemon.notice openvpn[407]: Initialization Sequence Completed
Cliente:
root@Portatil:/etc/openvpn# openvpn client.conf
Tue Jun 22 12:08:24 2010 OpenVPN 2.1.0 x86_64-pc-linux-gnu [SSL] [LZO2]
[EPOLL] [PKCS11] [MH] [PF_INET6] [eurephia] built on Jan 26 2010
Tue Jun 22 12:08:24 2010 NOTE: OpenVPN 2.1 requires ‘–script-security 2′ or higher to call user-defined scripts or executables
Tue Jun 22 12:08:24 2010 /usr/bin/openssl-vulnkey -q -b 2048 -m
Tue Jun 22 12:08:24 2010 Control Channel Authentication: using ‘ta.key’ as a OpenVPN static key file
Tue Jun 22 12:08:24 2010 Outgoing Control Channel Authentication: Using 160 bit message hash ‘SHA1′ for HMAC authentication
Tue Jun 22 12:08:24 2010 Incoming Control Channel Authentication: Using 160 bit message hash ‘SHA1′ for HMAC authentication
Tue Jun 22 12:08:24 2010 LZO compression initialized
Tue Jun 22 12:08:24 2010 Control Channel MTU parms [ L:1558 D:166 EF:66 EB:0 ET:0 EL:0 ]
Tue Jun 22 12:08:24 2010 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:135 ET:0 EL:0 AF:3/1 ]
Tue Jun 22 12:08:24 2010 Local Options hash (VER=V4): ’9e7066d2′
Tue Jun 22 12:08:24 2010 Expected Remote Options hash (VER=V4): ’162b04de’
Tue Jun 22 12:08:24 2010 Socket Buffers: R=[124928->131072] S=[124928->131072]
Tue Jun 22 12:08:24 2010 UDPv4 link local: [undef]
Tue Jun 22 12:08:24 2010 UDPv4 link remote: [AF_INET]XX:1194
Tue Jun 22 12:08:24 2010 TLS: Initial packet from [AF_INET]XX:1194, sid=0e6c8016 fc84b328
Tue Jun 22 12:08:27 2010 VERIFY OK: depth=1, /C=XX/ST=X/L=XX/O=Xa/CN=XX/emailAddress=XX.com
Tue Jun 22 12:08:27 2010 VERIFY OK: nsCertType=SERVER
Tue Jun 22 12:08:27 2010 VERIFY OK: depth=0, /C=XXX/ST=XX/L=xxx/O=xxxx/CN=xxx/emailAddress=xxx
Tue Jun 22 12:08:30 2010 Data Channel Encrypt: Cipher ‘AES-256-CBC’ initialized with 256 bit key
Tue Jun 22 12:08:30 2010 Data Channel Encrypt: Using 160 bit message hash ‘SHA1′ for HMAC authentication
Tue Jun 22 12:08:30 2010 Data Channel Decrypt: Cipher ‘AES-256-CBC’ initialized with 256 bit key
Tue Jun 22 12:08:30 2010 Data Channel Decrypt: Using 160 bit message hash ‘SHA1′ for HMAC authentication
Tue Jun 22 12:08:30 2010 Control Channel: TLSv1, cipher TLSv1/SSLv3 EDH-RSA-DES-CBC3-SHA, 2048 bit RSA
Tue Jun 22 12:08:30 2010 [servidor] Peer Connection Initiated with [AF_INET]87.220.30.11:1194
Tue Jun 22 12:08:33 2010 SENT CONTROL [servidor]: ‘PUSH_REQUEST’ (status=1)
Tue Jun 22 12:08:33 2010 PUSH: Received control message:
‘PUSH_REPLY,route 10.10.3.0 255.255.255.0,dhcp-option DOMAIN
RED_LOCAL,dhcp-option DNS 10.10.3.1,redirect-gateway def1,route
10.8.0.1,topology net30,ping 15,ping-restart 60,ifconfig 10.8.0.6
10.8.0.5′
Tue Jun 22 12:08:33 2010 OPTIONS IMPORT: timers and/or timeouts modified
Tue Jun 22 12:08:33 2010 OPTIONS IMPORT: –ifconfig/up options modified
Tue Jun 22 12:08:33 2010 OPTIONS IMPORT: route options modified
Tue Jun 22 12:08:33 2010 OPTIONS IMPORT: –ip-win32 and/or –dhcp-option options modified
Tue Jun 22 12:08:33 2010 ROUTE default_gateway=10.10.2.1
Tue Jun 22 12:08:33 2010 TUN/TAP device tun0 opened
Tue Jun 22 12:08:33 2010 TUN/TAP TX queue length set to 100
Tue Jun 22 12:08:33 2010 /sbin/ifconfig tun0 10.8.0.6 pointopoint 10.8.0.5 mtu 1500
Tue Jun 22 12:08:33 2010 /sbin/route add -net xxx netmask 255.255.255.255 gw 10.10.2.1
Tue Jun 22 12:08:33 2010 /sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 10.8.0.5
Tue Jun 22 12:08:33 2010 /sbin/route add -net 128.0.0.0 netmask 128.0.0.0 gw 10.8.0.5
Tue Jun 22 12:08:33 2010 /sbin/route add -net 10.10.3.0 netmask 255.255.255.0 gw 10.8.0.5
Tue Jun 22 12:08:33 2010 /sbin/route add -net 10.8.0.1 netmask 255.255.255.255 gw 10.8.0.5
Tue Jun 22 12:08:33 2010 Initialization Sequence Completed
Ahora tenemos tres opciones para conectaros a la VPN:
- Tecleando en consola el comando “sudo openvpn cliente.conf” y no cerrando la consola (ya que si no cierra la conexión).
- Automatizando el inicio de la VPN en el sistema, con lo cual
siempre pasarás por la VPN aunque la red sea segura, y eso conlleva no
tener la máxima velocidad posible (redirigimos internet).
- Poniendo OpenVPN en el network manager de forma gráfica y ada vez que queramos conectarnos dar 2 clicks y listo.
Esta última forma es la más útil al menos para mí, os voy a poner como hacerlo.
Usar Network-Manager para hacer la conexión OpenVPN (con gráficos y sin consola).
Vamos a instalar OpenVPN para el network-manager (plugin).
sudo apt-get install network-manager-openvpn
SOLUCIÓN a: Openvpn falló porque no había secretos vpn válidos
Una vez instalado (y reiniciado el sistema a ser posible) hacemos:
sudo gedit /etc/dbus-1/system.d/nm-openvpn-service.conf
Y debe poner obligatoriamente lo siguiente:
“-//freedesktop//DTD D-BUS Bus Configuration 1.0//EN”
“http://www.freedesktop.org/standards/dbus/1.0/busconfig.dtd”>
Guardáis datos, salís del gedit y reiniciáis el ordenador (también
vale reiniciar sólo el network-manager pero tardas menos así), ya nos os
dará el famoso error de: Openvpn falló porque no había secretos vpn
válidos.
Nota:
Realmente lo único que haces es intercalar esta línea de código:
Entre las otras dos, pero os puse el código entero para que no os compliquéis la vida.
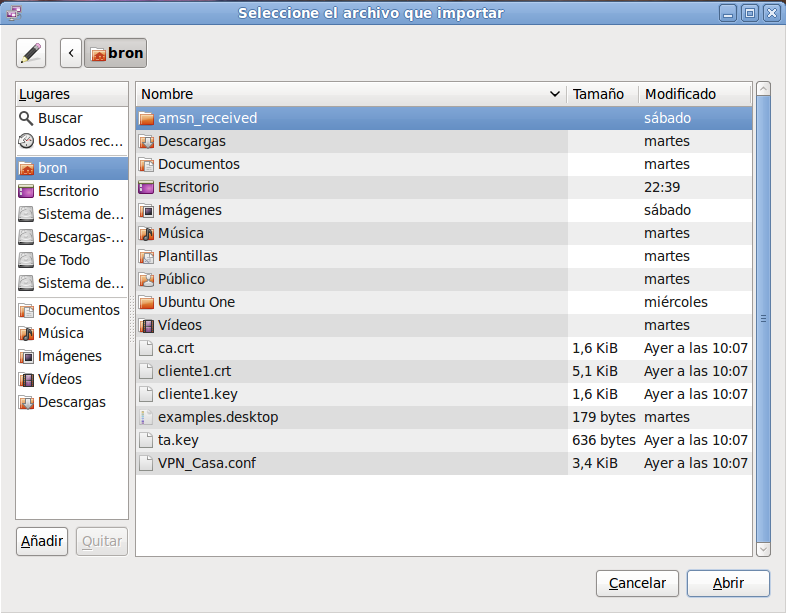
Ya tenemos el plugin openvpn para network manager puesto a punto para configurarlo, ahora vamos a importar la configuración
cliente.conf de tal forma que en 4 clicks tengamos todo listo.
En esta pantalla seleccionamos “
Importar“:

Buscamos el archivos .CONF y doble click:
A continuación y SIN TOCAR NADA, le damos a APLICAR:
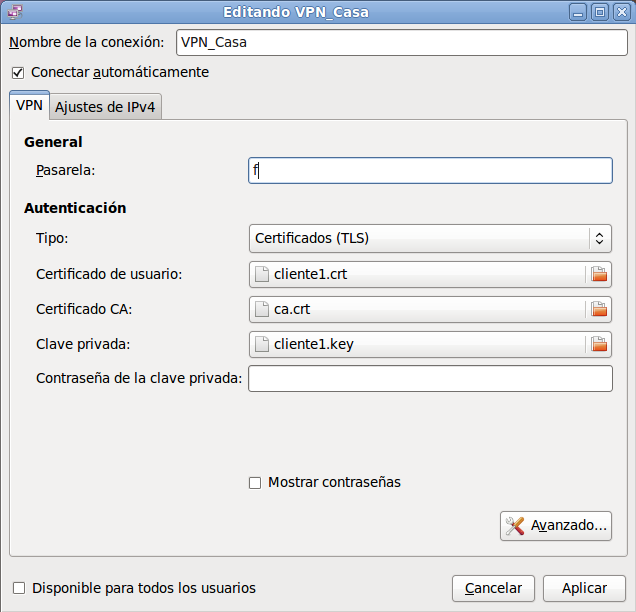
Y ya la habremos importado:
Una vez que hemos hecho esto, basta con dar click izquierdo sobre el
network-manager, nos vamos a conexiones VPN y seleccionamos la conexión
que hemos importado anteriormente, en 15 segundos estaremos conectados y
nos podrá un candado sobre el network-manager, si no funciona ejecutad
el cliente.conf manualmente con el siguiente comando (si tampoco
conecta, repasa los archivos .CONF).
sudo openvpn cliente.conf
Nota: aquí tenéis el HOWTO oficial de OpenVPN:
http://openvpn.net/index.php/open-source/documentation/howto.html
Windows 7
La creación de los certificados es exactamente en Windows que en
GNU/Linux, sólo cambian los comandos a usar, incluso podéis hacer los
certificados en GNU/Linux y llevarlos a Windows sin cambiar de
extensión, únicamente el server.conf y cliente.conf han de pasar a
extensión .ovpn, nada más.
Lo primero que vamos a hacer es bajarnos la última versión de OpenVPN y configurar el GUI adecuadamente.
Descargamos la última versión OpenVPN desde aquí:
http://openvpn.net/index.php/open-source/downloads.html
La instalamos normalmente, con derechos de administrador (por
supuesto), una vez instalado todo, reiniciamos el equipo (aunque no es
necesario).
Ahora nos vamos al icono del escritorio y pulsamos
click derecho sobre él y seleccionamos
PROPIEDADES, en la pestaña
COMPATIBILIDADModo de Compatibilidad para Windows XP (Service Pack 3) Ejecutar como administrador“, tal y como tenéis en la imagen: seleccionamos y seleccionamos la casilla de ”
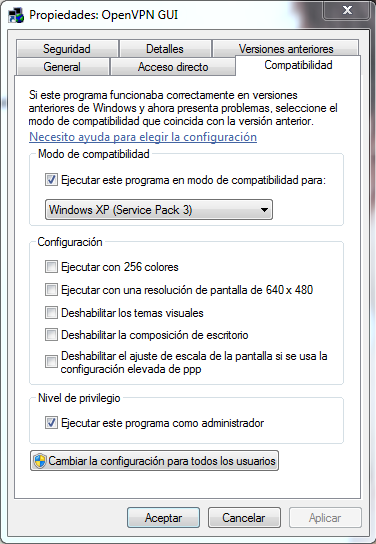
Y ya os debería funcionar correctamente, si os funciona sin hacer esto pues perfecto, pero a mí no me funcionó.
Generar la llave y el certificado para la Autoridad Certificadora (CA).
Ejecutamos el CMD.EXE con permisos de administrador (clic derecho ejecutar como administrador).
Nos vamos al directorio de trabajo de OpenVPN carpeta easy-rsa con el comando cd.
- Renombramos vars.bat.sample a vars.bat y lo abrimos con el bloc de notas para rellenar las key_country, key_province etc.
- El tamaño de la llave RSA es controlado por la variable
KEY_SIZE en el archivo vars, por tanto en lugar de tener 1024 (bits), ponemos 2048 (bits) si queréis más seguridad (recomiendo 2048).
Salimos y guardamos.
Ejecutamos el comando vars (en c:\archivos de programa\openvpn\easy-rsa)
A continuación ejecutamos clean-all.bat, nos creará una carpeta nueva “keys” donde almacenaremos las claves.
Parámetros Diffie Hellman
Vamos a generar estos parámetros necesarios para el servidor.
Ejecutamos el comando: build-dh y empezará el proceso.
Creación certificado para la CA
Renombramos openssl.sample a openssl (sin el sample).
Ejecutamos en consola
build-ca para crearlo y ponéis
lo mismo que habéis rellenado en vars (key_country etc) y cuando te
pida common name poned openvpn-ca (por ejemplo).
Generación de certificado y llaves para el SERVER
Ejecutamos: build-key-server server para crear el servidor, el common name se obtiene del segundo “server”.
Generación de certificado y llaves para el CLIENTE
Ejecutamos:
build-key cliente1 para crear el primer cliente y así con los demás que queramos.
Generar llave TLS-AUTH
En el directorio easy-rsa ejecutamos:
openvpn –genkey –secret ta.key y se nos pondrá en ese mismo directorio.
Nota: son dos guiones, no uno sólo.
Ahora nos toca configurar el
client.ovpn (client.conf en GNU/Linux) con esto, se hace exactamente igual que en GNU/Linux y tiene las mismas opciones y TODO IGUAL.
El servidor es también igual que en GNU/Linux.
Los archivos que debéis pasar al servidor y clientes, hacedlo por un medio seguro con las .key.
Aquí tenéis la misma tabla que puse arriba:

Aquí tenéis el manual oficial de OpenVPN:
http://openvpn.net/index.php/open-source/documentation/howto.html
Pruebas de conectividad e iniciación:
Como supongo que usaréis Windows como cliente para conectaros a una
VPN que esté en un servidor con GNU/Linux o en un router con firmwares
de terceros, os voy a enseñar como arrancarlo mediante la interfaz
gráfica.
Copiamos
ca.crt, cliente1.crt, cliente1.key, ta.key y cliente.ovpn
a la carpeta Openvpn/config/, en el cliente.ovpn no hace falta poner la
ruta entera de ca.crt y todos los demás, ya que están en la misma
carpeta.
Una vez que ya tenemos el servidor a punto, todos los archivos del
cliente en la carpeta config, iniciamos el OpenVPN GUI que tenemos en el
escritorio.
Recuerda: ejecuta en modo de compatibilidad XP Service Pack 3 y con derechos de administrador.
Clic derecho sobre el icono y pulsamos connect, esperamos hasta que se conecte y nos de
LUZ VERDE (si hacemos click derecho sobre el icono y le damos a “Show Status” nos mostrará el LOG de conexión).

Y ya estamos conectados a la VPN en Windows 7.
Espero que os haya gustado…y si tenéis alguna pregunta hacedla y os responderé (si sé).
Manual realizado por Sergio de Luz (Bron) para REDESZone.net






























 LibreOffice
LibreOffice Firefox
Firefox