Helix3 vs Helix3 Pro
Helix2008R1.iso http://mirrors.cmich.edu/helix/
Source
Helix 2009 R1 ISO locally hosted here.
Source
Windows mode
In this mode, Helix is used just as any other CD inside Windows. Double-click to launch the application. You'll be warned about your actions.
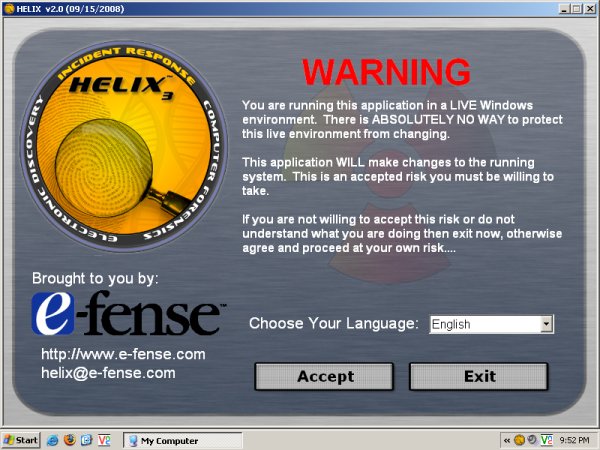
The Windows mode differs from the Linux side in being a floating application rather than a complete operating system. Therefore, the navigation is a little different.
First, you have the Quick Launch.
Then, there is the Page menu, which allows you to browse different categories of tools.
The Windows side contains a broad range of highly useful utilities.
The Incident Response page is particularly rich, with lots of excellent programs. Did I say you should be knowledgeable and extremely careful when running these tools, as you can very easily obliterate your system and even cause significant damage to the LAN? There, I said it.
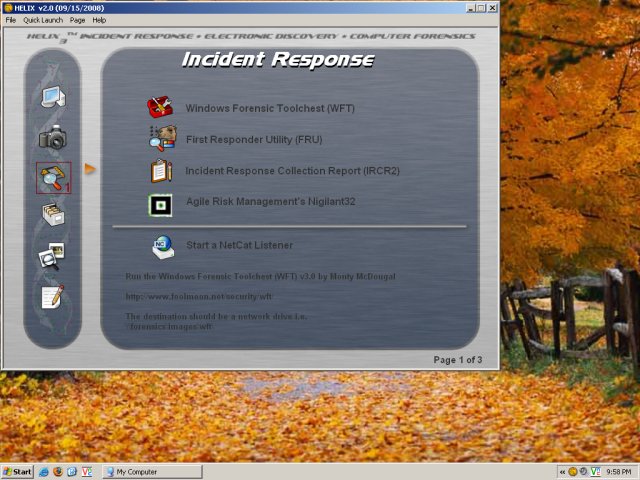
An entire section is dedicated to viewing (and retrieving) passwords, cookies and logs.

You also have tools for auditing of the system, remote connection (including VNC, SSH), file recovery, and rootkit scanning.
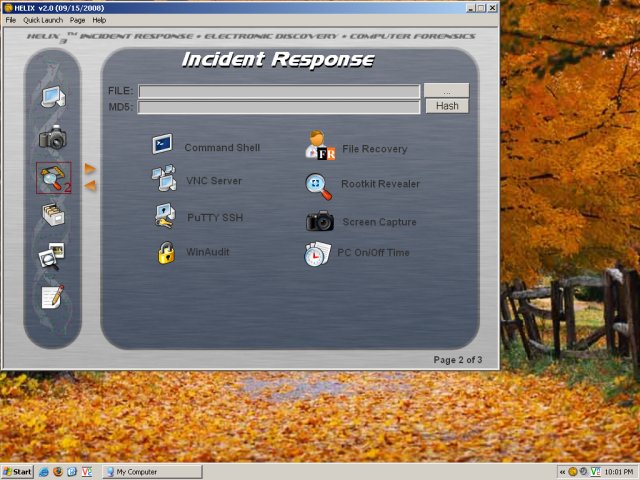
Like in Linux, it is possible to acquire entire disk drives (and even the physical memory).
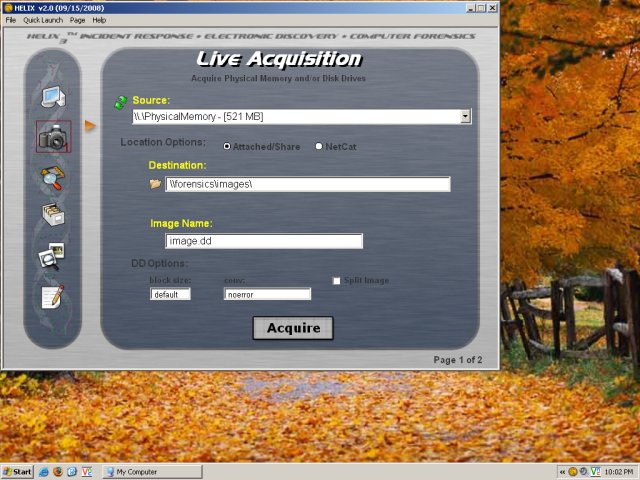
You can also browse contents of files and folders, calculate hashes, check time stamps, and more. This allows you to look for suspicious, clandestine activities in your data archives.
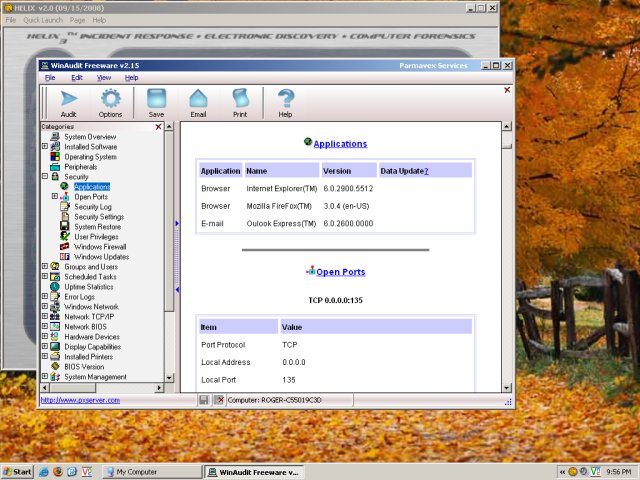
As mentioned earlier, you can run full audits of your system.
Conclusion Helix is a highly useful toolbox. The dual mode is especially valuable, since quite a few system administrators are not that proficient in Linux. Furthermore, it allows Helix users to approach Windows-related problems with several methods, first trying to cope with problems while still logged in Windows and then escalating to the Linux live CD mode.
Helix is a stable, complete package, with a broad range of great utilities that will significantly increase your ability to respond to problems, threats and incidents in your environment.
For more details about forensics in general, please see the Introduction.



 LibreOffice
LibreOffice Firefox
Firefox
No comments:
Post a Comment