Finding Network printers using Nmap and SNMP tools
Using Nmap from your Linux (preferable) or Windows box makes finding JetDirects and other network printers pretty easy. The Nmap commands I will be showing in this section are very simple and not very stealthy so you may want to consult the Nmap MAN page or a good Nmap tutorial for more ideas. You could use a simple Nmap command like:
nmap -A 192.168.1.*
to scan the range 192.168.1.1-255 for common ports and do an OS and version detect on the systems it finds. The output of the above command would look something like the following:
| Irongeek:~# nmap -A 192.168.1.* Starting nmap 3.81 ( http://www.insecure.org/nmap/ ) at 2005-09-08 15:12 EDT Interesting ports on igprinter (192.168.1.93): (The 1656 ports scanned but not shown below are in state: closed) PORT STATE SERVICE VERSION 21/tcp open ftp HP JetDirect ftpd 23/tcp open telnet? 80/tcp open http HP Jetdirect httpd 280/tcp open http HP Jetdirect httpd 515/tcp open sdmsvc LANDesk Software Distribution (sdmsvc.exe) 631/tcp open http HP Jetdirect httpd 9100/tcp open jetdirect? Device type: printer|print server Running: HP embedded OS details: HP LaserJet printer/print server Nmap finished: 1 IP address (1 host up) scanned in 120.963 seconds Irongeek:~# |
================
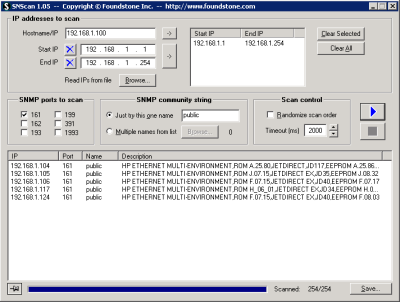
Foundstone's SNScan in another good choice:
SNScan v1.05
SNMP Detection Utility
SNMP Detection Utility
SNScan is a Windows based SNMP detection utility that can quickly and accurately identify SNMP enabled devices on a network. This utility can effectively indicate devices that are potentially vulnerable to SNMP related security threats, such as those released on February 12, 2002 and the Cisco IPv4 Remote Denial of Service vulnerability from July 17, 2003.
SNScan allows for the scanning of SNMP specific ports (e.g. UDP 161, 193, 391 and 1993) and the use of standard (i.e. "public") as well as user-defined SNMP community names. User-defined community names may be used to more effectively evaluate the presence of SNMP enabled devices in more complex networks.
SNScan is intended for use by system and network administrators as a fast and reliable utility for information gathering. While not indicating whether SNMP enabled devices are vulnerable to specific threats, SNScan can quickly and accurately identify potential areas of exposure to SNMP related vulnerabilities.
====================
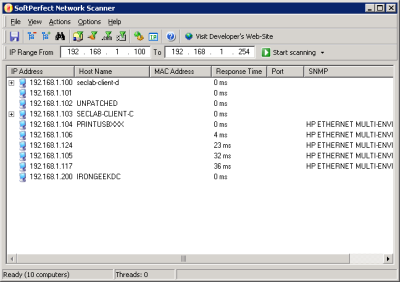
or Softperfect's NetScan if you turn on the SNMP search options:
SoftPerfect Network Scanner is a free multi-threaded IP, NetBIOS and SNMP scanner with a modern interface and many advanced features. It is intended for both system administrators and general users interested in computer security. The program pings computers, scans for listening TCP/UDP ports and displays which types of resources are shared on the network (including system and hidden).
In addition, it allows you to mount shared folders as network drives, browse them using Windows Explorer, filter the results list and more. SoftPerfect Network Scanner can also check for a user-defined port and report back if one is open. It can also resolve host names and auto-detect your local and external IP range. It supports remote shutdown and Wake-On-LAN.
Key features
- Pings computers and displays those alive.
- Detects hardware MAC-addresses, even across routers.
- Detects hidden shared folders and writable ones.
- Detects your internal and external IP addresses.
- Scans for listening TCP ports, some UDP and SNMP services.
- Retrieves currently logged-on users, configured user accounts, uptime, etc.
- You can mount and explore network resources.
- Can launch external third party applications.
- Exports results to HTML, XML, CSV and TXT
- Supports Wake-On-LAN, remote shutdown and sending network messages.
- Retrieves potentially any information via WMI.
- Retrieves information from remote registry, file system and service manager.
- It is absolutely free, requires no installation, and does not contain any adware/spyware/malware.
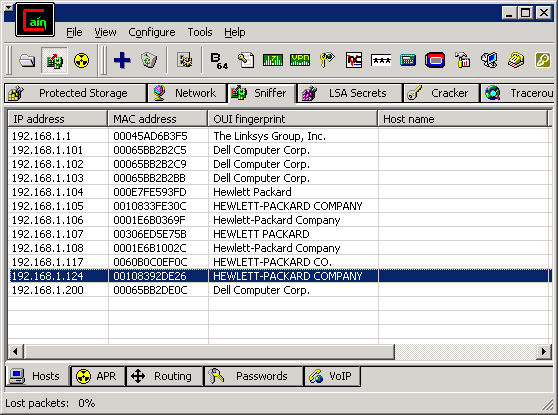
Another third way you could find network printers (if you are on the same subnet) is to use Nmap or Cain to do an ARP sweep and look for and boxes with a MAC address belonging to Hewlett Packard, Ricoh or another printer vendor. These are likely network printers.
=======================
Finding Printers with Google
Sometimes for convenience admins will put links to there printers' web interfaces on an Intranet site so they can easily admin them or pull off stored documents. Well, sometimes an Intranet is not really just an Intranet but accessible via the Internet. Google is a great way to find these printers. Here are a few search strings that may be of interest:
....
HP Jetdirects (Varies greatly from model to model)
CUPS Connected Printers
Try combining the above with the Google "site:" parameter to restrict the search to just certain organizations. For more information on Google Hacking visit http://johnny.ihackstuff.com and search their database of useful Google search strings for "Printers". I obtained some of the above search strings from Johnny's site.
==========
Finding info about the printer using SNMP tools
Using the tools from http://net-snmp.sourceforge.net on a Linux box can yield a great deal of information about a network, assuming no firewalls are blocking the SNMP port (161/udp). The greatly truncated output below should give you some idea as to the kind of information you can get using snmpwalk, including other hosts on the same network, their IPs and MAC addresses and the features of the printer along with it's firmware revision. If you are using a Debian based distribution on Linux try the "apt-get install snmp" command to get these tools.
root@Cthulhu:~# snmpwalk -v 1 -c public 192.168.1.2 SNMPv2-MIB::sysDescr.0 = STRING: HP ETHERNET MULTI-ENVIRONMENT,ROM H_06_01,JETDIRECT EX,JD34,EEPROM H.08.49 SNMPv2-MIB::sysObjectID.0 = OID: SNMPv2-SMI::enterprises.11.2.3.9.1 SNMPv2-MIB::sysUpTime.0 = Timeticks: (1358074910) 157 days, 4:25:49.10 SNMPv2-MIB::sysContact.0 = STRING: SNMPv2-MIB::sysName.0 = STRING: NPI6D47C6 SNMPv2-MIB::sysLocation.0 = STRING: SNMPv2-MIB::sysServices.0 = INTEGER: 64 IF-MIB::ifNumber.0 = INTEGER: 1 IF-MIB::ifIndex.1 = INTEGER: 1 IF-MIB::ifDescr.1 = STRING: HP ETHERNET MULTI-ENVIRONMENT,ROM H_06_01,JETDIRECT EX,JD34,EEPROM H.08.49 IF-MIB::ifType.1 = INTEGER: ethernetCsmacd(6) ...Omitted for security and space reasons... IF-MIB::ifOutQLen.1 = Gauge32: 0 IF-MIB::ifSpecific.1 = OID: SNMPv2-SMI::zeroDotZero.0 RFC1213-MIB::atIfIndex.1.1.192.168.19.16 = INTEGER: 1 ...Omitted for security and space reasons... RFC1213-MIB::atIfIndex.1.1.192.168.31.254 = INTEGER: 1 RFC1213-MIB::atIfIndex.1.1.24.0.1.60 = INTEGER: 1 RFC1213-MIB::atPhysAddress.1.1.192.168.19.16 = Hex-STRING: 00 0A 95 A6 6C 00 ...Omitted for security and space reasons... RFC1213-MIB::atPhysAddress.1.1.192.168.31.254 = Hex-STRING: 00 0F 34 E8 DC 38 RFC1213-MIB::atPhysAddress.1.1.24.0.1.60 = Hex-STRING: 01 00 5E 00 01 3C RFC1213-MIB::atNetAddress.1.1.192.168.19.16 = Network Address: 95:A0:13:10 ...Omitted for security and space reasons... RFC1213-MIB::atNetAddress.1.1.192.168.31.254 = Network Address: 95:A0:1F:FE RFC1213-MIB::atNetAddress.1.1.24.0.1.60 = Network Address: E0:00:01:3C IP-MIB::ipForwarding.0 = INTEGER: notForwarding(2) I...Omitted for security and space reasons... IP-MIB::ipAdEntAddr.192.168.1.2 = IpAddress: 192.168.1.2 ...Omitted for security and space reasons... IP-MIB::ipNetToMediaIfIndex.1.192.168.19.16 = INTEGER: 1 I...Omitted for security and space reasons... IP-MIB::ipNetToMediaIfIndex.1.192.168.31.254 = INTEGER: 1 IP-MIB::ipNetToMediaIfIndex.1.24.0.1.60 = INTEGER: 1 IP-MIB::ipNetToMediaPhysAddress.1.192.168.19.16 = STRING: 0:a:95:a6:6c:0 ...Omitted for security and space reasons... IP-MIB::ipNetToMediaPhysAddress.1.192.168.31.254 = STRING: 0:f:34:e8:dc:38 ...Omitted for security and space reasons... IP-MIB::ipNetToMediaNetAddress.1.192.168.31.254 = IpAddress: 192.168.31.254 ...Omitted for security and space reasons... IP-MIB::ipNetToMediaType.1.192.168.31.254 = INTEGER: dynamic(3) IP-MIB::ipNetToMediaType.1.24.0.1.60 = INTEGER: dynamic(3) IP-MIB::ipRoutingDiscards.0 = Counter32: 2801 ...Omitted for security and space reasons... IP-MIB::icmpOutAddrMaskReps.0 = Counter32: 0 TCP-MIB::tcpRtoAlgorithm.0 = INTEGER: vanj(4) TCP-MIB::tcpRtoMin.0 = INTEGER: 10 milliseconds TCP-MIB::tcpRtoMax.0 = INTEGER: 120000 milliseconds ...Omitted for security and space reasons... TCP-MIB::tcpRetransSegs.0 = Counter32: 20 TCP-MIB::tcpConnState.192.168.1.2.21.0.0.0.0.0 = INTEGER: listen(2) TCP-MIB::tcpConnLocalAddress.192.168.1.2.21.0.0.0.0.0 = IpAddress: 192.168.1.2 TCP-MIB::tcpConnLocalPort.192.168.1.2.21.0.0.0.0.0 = INTEGER: 21 TCP-MIB::tcpConnRemAddress.192.168.1.2.21.0.0.0.0.0 = IpAddress: 0.0.0.0 TCP-MIB::tcpConnRemPort.192.168.1.2.21.0.0.0.0.0 = INTEGER: 0 TCP-MIB::tcpInErrs.0 = Counter32: 0 TCP-MIB::tcpOutRsts.0 = Counter32: 17832 UDP-MIB::udpInDatagrams.0 = Counter32: 8374653 UDP-MIB::udpNoPorts.0 = Counter32: 8135924 UDP-MIB::udpInErrors.0 = Counter32: 22054 UDP-MIB::udpOutDatagrams.0 = Counter32: 363574 UDP-MIB::udpLocalAddress.0.0.0.0.68 = IpAddress: 0.0.0.0 UDP-MIB::udpLocalPort.0.0.0.0.68 = INTEGER: 68 UDP-MIB::udpLocalAddress.192.168.1.2.137 = IpAddress: 192.168.1.2 |
The above command works well on Jetdirects, Richo Savins and other common network printers that support SNMP. If you don't know the proper SNMP community name a quick sniff of the network with Ettercap or Dsniff should revel it to you iif the admin is using using SNMP version 1 or 2. Most times the community name will just be the default "public".



 LibreOffice
LibreOffice Firefox
Firefox
No comments:
Post a Comment