by Jake Soriano (Technical Communications)
Trend Micro researchers discovered that warez and crack web pages are being used by cybercriminals as download sites for malware related to VIRUT and VIRUX. Searches for serial numbers, cracks, and even antivirus products like Trend Micro yield malcodes that come in the form of executables or self-extracting files.
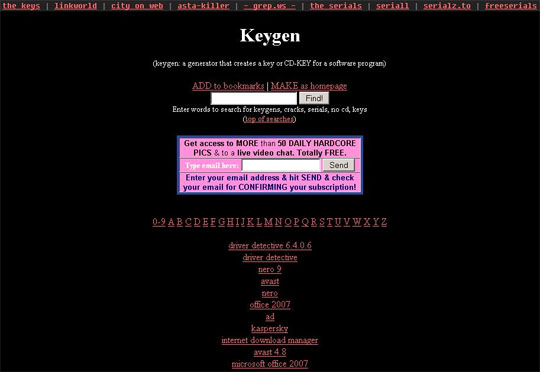 Figure 1. Crack sites are being used for malware distribution.
Figure 1. Crack sites are being used for malware distribution.Besides the search results, quick links in these sites also lead to malicious files. Ads and banners are also infection vectors. Ad placeholders are commonly found in legitimate websites, and it only takes a nifty social engineering technique to trick unknowing users into clicking. Embedded in these ads are IFrames with encypted links that lead to dangerous websites.
The downloaded malware include variants under the FAKEAV, TDSS, and VUNDO families. Infection chains, however, are notable for the presence of VIRUT and VIRUX malware. VIRUX and VIRUT attacks were initially about the volume of infected PCs. The numbers are massive enough to worry Web users and security researchers: around 20,000 PCs are infected per day.
Trend Micro’s earlier blog post on the rising number of VIRUX-related cases describes the complicated infection chain triggered when VIRUX infects a system. But this current threat reveals that more than the information stealing payload associated with these infectors, they also download malware with with rogue antivirus routines.
Our engineers are still analyzing this threat further. Updates will be posted as soon as more information becomes available. Users are advised to not click links in suspicious ads and to refrain from downloading installer files.



 LibreOffice
LibreOffice Firefox
Firefox
No comments:
Post a Comment