Source
http://ekiga.org/?rub=5
Sunday, October 31, 2010
Saturday, October 30, 2010
IIS -directorios virtuales
En la mayoría de casos, el contenido que se publica en el sitio Web o FTP se encuentra en un directorio raíz o principal de su equipo, por ejemplo C:\Inetpub\Wwwroot\. Puede haber casos en que el contenido se encuentre en otro lugar o incluso en un equipo remoto.
Para publicar desde cualquier directorio que no esté contenido en el directorio principal o directorio raíz, puede crear un directorio virtual. Un directorio virtual es un directorio que no está en el directorio particular pero que aparece en los exploradores de los clientes como si estuviera.
 Importante Debe ser miembro del grupo Administradores en el equipo local para poder llevar a cabo el procedimiento o procedimientos siguientes, o debe tener delegada la autoridad correspondiente. Como práctica de seguridad recomendada, inicie sesión en el equipo con una cuenta que no pertenezca al grupo Administradores y, después, utilice el comando Ejecutar como para ejecutar el Administrador de IIS como Administrador. En el símbolo del sistema, escriba
Importante Debe ser miembro del grupo Administradores en el equipo local para poder llevar a cabo el procedimiento o procedimientos siguientes, o debe tener delegada la autoridad correspondiente. Como práctica de seguridad recomendada, inicie sesión en el equipo con una cuenta que no pertenezca al grupo Administradores y, después, utilice el comando Ejecutar como para ejecutar el Administrador de IIS como Administrador. En el símbolo del sistema, escriba
runas /user:nombre_cuenta_administrativa "mmc %systemroot%\system32\inetsrv\iis.msc".
Para publicar desde cualquier directorio que no esté contenido en el directorio principal o directorio raíz, puede crear un directorio virtual. Un directorio virtual es un directorio que no está en el directorio particular pero que aparece en los exploradores de los clientes como si estuviera.
 Importante Debe ser miembro del grupo Administradores en el equipo local para poder llevar a cabo el procedimiento o procedimientos siguientes, o debe tener delegada la autoridad correspondiente. Como práctica de seguridad recomendada, inicie sesión en el equipo con una cuenta que no pertenezca al grupo Administradores y, después, utilice el comando Ejecutar como para ejecutar el Administrador de IIS como Administrador. En el símbolo del sistema, escriba
Importante Debe ser miembro del grupo Administradores en el equipo local para poder llevar a cabo el procedimiento o procedimientos siguientes, o debe tener delegada la autoridad correspondiente. Como práctica de seguridad recomendada, inicie sesión en el equipo con una cuenta que no pertenezca al grupo Administradores y, después, utilice el comando Ejecutar como para ejecutar el Administrador de IIS como Administrador. En el símbolo del sistema, escribarunas /user:nombre_cuenta_administrativa "mmc %systemroot%\system32\inetsrv\iis.msc".
Para crear un directorio virtual
Si está utilizando el sistema de archivos NTFS, también puede crear un directorio virtual.- En el Administrador de IIS, expanda la carpeta Sitios FTP, expanda el sitio FTP al que desea agregar un directorio virtual, haga clic con el botón secundario en el sitio o la carpeta desde la que desea crear el directorio virtual, seleccione Nuevo y haga clic en Directorio virtual. Aparece el Asistente para crear un directorio virtual.
- Haga clic en Siguiente.
- En el cuadro de texto Alias, escriba un nombre para el directorio virtual. Éste es el nombre que escribe el usuario; debe ser corto y fácil de escribir.
- Haga clic en Siguiente.
- En el cuadro Ruta, escriba o explore el directorio físico que contiene el directorio virtual y después haga clic en Siguiente.
- En Habilitar los siguientes permisos, active las casillas de verificación para los permisos de acceso que desee asignar a los usuarios y haga clic en Siguiente.
 Nota Por motivos de seguridad, cuando seleccione los permisos de acceso, considere la posibilidad de habilitar sólo el permiso predeterminado Lectura. Al restringir los permisos de esta forma, puede evitar ataques contra su sitio Web por usuarios malintencionados. Para obtener más información, vea Proteger los directorios virtuales y Control de acceso en la ayuda de Windows.
Nota Por motivos de seguridad, cuando seleccione los permisos de acceso, considere la posibilidad de habilitar sólo el permiso predeterminado Lectura. Al restringir los permisos de esta forma, puede evitar ataques contra su sitio Web por usuarios malintencionados. Para obtener más información, vea Proteger los directorios virtuales y Control de acceso en la ayuda de Windows.
- Haga clic en Finalizar. El directorio virtual se ha creado debajo del nivel actual de la carpeta seleccionada.
Para crear un directorio virtual con NTFS
- Abra el Explorador de Windows.
- Haga clic con el botón secundario del mouse (ratón) en la carpeta que desea como directorio virtual y haga clic en Compartir y seguridad.
- Haga clic en la ficha Uso compartido de Web.
- Haga clic en Compartir esta carpeta.
- En el cuadro de texto Alias, escriba el nombre para el directorio virtual.
- Haga clic en Aceptar dos veces.
Temas relacionados
- Para conocer una forma alternativa de crear un directorio virtual Web, vea Crear directorios virtuales Web.
- Para conocer una forma alternativa de crear un directorio virtual FTP, vea Crear directorios virtuales FTP.
Friday, October 29, 2010
Convert DHCP configuration to static IP configuration
based on this source (for Ubuntu)
Desired new sample settings:
= Host IP address
= Netmask:
= Network ID:
= Broadcast IP:
= Gateway/Router IP:
= DNS Server: 8.8.8.8
Find and remove dhcp entry:
Append new network settings:
Save and close the file. Restart the network:
Task: Define new DNS servers Open /etc/resolv.conf file
You need to remove old DNS server assigned by DHCP server:
Save and close the file.
Task: Test DNS server
Network command line cheat sheet You can also use commands to change settings. Please note that these settings are temporary and not the permanent. Use above method to make network changes permanent or GUI tool as described below.
Task:
Display network interface information
Task:
Take down network interface eth0
/ take a network interface down
OR
Task:
Bring a network interface eth0 up
OR
Task: Change IP address and netmask from command lineActivate network interface eth0 with a new IP (192.168.1.50) / netmask:
Task: Display the routing table
OR
Output:
Task: Display current active Internet connections
(servers and established connection)
Task: Display open ports
OR
Task: Display network interfaces stats (RX/TX etc)
Task: Display output for active/established connections only
$ netstat -e
Where
Send ICMP ECHO_REQUEST to network hosts, routers, servers etc with ping command. This verifies connectivity exists between local host and remote network system:
See simple Linux system monitoring with ping command and scripts for more information.
Task: Use GUI (Graphical Configuration) network Tool If you are new, use GUI configuration tool, type the following command at terminal:
Above command is Ubuntu's GUI for configuring network connections tool.
Final tip - Learn how find out more information about commandsA man page is your best friend when you wanted to learn more about particular command or syntax. For example, read detailed information about ifconfig and netstat command:
Find out what command is used for particular task by searching the short descriptions and manual page names for the keyword:
Display short descriptions of a command:
Desired new sample settings:
= Host IP address
200.87.229.20= Netmask:
255.255.255.252= Network ID:
200.87.229.0= Broadcast IP:
200.87.229.255= Gateway/Router IP:
200.87.229.17= DNS Server: 8.8.8.8
Open network configuration file:
sudo nano /etc/network/interfacesiface eth0 inet dhcpAppend new network settings:
iface eth0 inet static
address 200.87.229.20
netmask 255.255.255.252
network 200.87.229.0 broadcast 200.87.229.255
gateway 200.87.229.17Save and close the file. Restart the network:
$ sudo /etc/init.d/networking restartTask: Define new DNS servers Open /etc/resolv.conf file
$ sudo nano /etc/resolv.conf You need to remove old DNS server assigned by DHCP server:
search myisp.com
nameserver 200.87.229.254 nameserver 8.8.8.8Save and close the file.
Task: Test DNS server
$ host cyberciti.bizNetwork command line cheat sheet You can also use commands to change settings. Please note that these settings are temporary and not the permanent. Use above method to make network changes permanent or GUI tool as described below.
Task:
Display network interface information
$ ifconfigTask:
Take down network interface eth0
/ take a network interface down
$ sudo ifconfig eth0 downOR
$ sudo ifdown eth0 Task:
Bring a network interface eth0 up
$ sudo ifconfig eth0 upOR
$ sudo ifup eth0 Task: Change IP address and netmask from command lineActivate network interface eth0 with a new IP (192.168.1.50) / netmask:
$ sudo ifconfig eth0 192.168.1.50 netmask 255.255.255.0 upTask: Display the routing table
$ /sbin/route OR
$ /sbin/route -nOutput:
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface localnet * 255.255.255.0 U 0 0 0 ra0
200.87.229.0 * 255.255.255.0 U 0 0 0 eth0
172.16.236.0 * 255.255.255.0 U 0 0 0 eth1 default 200.87.229.254 0.0.0.0 UG 0 0 0 ra0Task: Add a new gateway
$ sudo route add default gw 172.16.236.0Task: Display current active Internet connections
(servers and established connection)
$ netstat -natTask: Display open ports
$ sudo netstat -tulpOR
$ sudo netstat -tulpnTask: Display network interfaces stats (RX/TX etc)
$ netstat -iTask: Display output for active/established connections only
$ netstat -e
$ netstat -te
$ netstat -tue
Where
- -t : TCP connections
- -u : UDP connections
- -e : Established
Send ICMP ECHO_REQUEST to network hosts, routers, servers etc with ping command. This verifies connectivity exists between local host and remote network system:
$ ping router
$ ping 192.168.1.254
$ ping cyberciti.bizSee simple Linux system monitoring with ping command and scripts for more information.
Task: Use GUI (Graphical Configuration) network Tool If you are new, use GUI configuration tool, type the following command at terminal:
$ network-admin &Above command is Ubuntu's GUI for configuring network connections tool.
Final tip - Learn how find out more information about commandsA man page is your best friend when you wanted to learn more about particular command or syntax. For example, read detailed information about ifconfig and netstat command:
$ man ifconfig
$ man netstat
Just get a short help with all command options by appending --help option to each command:$ netstat --helpFind out what command is used for particular task by searching the short descriptions and manual page names for the keyword:
$ man -k 'delete directory'
$ apropos -s 1 removeDisplay short descriptions of a command:
$ whatis rm
$ whatis netstat
Thursday, October 28, 2010
Network Information Services (NIS) and NFS
Source
Network Information Services (NIS) enables you to create user accounts that can be shared across all systems on your network. The user account is created only on the NIS server. NIS clients download the necessary username and password data from the NIS server to verify each user login.
An advantage of NIS is that users need to change their passwords on the NIS server only, instead of every system on the network. This makes NIS popular in computer training labs, distributed software development projects or any other situation where groups of people have to share many different computers.
The disadvantages are that NIS doesn't encrypt the username and password information sent to the clients with each login and that all users have access to the encrypted passwords stored on the NIS server. A detailed analysis of NIS security is beyond the scope of this book, but I suggest that you restrict its use to highly secure networks or to networks where access to non-NIS networks is highly restricted.
The Lightweight Directory Access Protocol (LDAP) offers similar features to NIS but has the advantage of supporting encryption without additional software and can support clients across multiple networks without the need for slave servers. It is for this reason that LDAP has become increasingly popular for this type of application. LDAP is discussed in more detail in Chapter 31, "Centralized Logins Using LDAP and RADIUS".
Contents
- 1 Sponsors
- 2 Introduction
- 3 Scenario
- 4 Configuring The NFS Server
- 5 Configuring The NFS Client
- 6 Configuring The NIS Server
- 7 Adding New NIS Users
- 8 Configuring The NIS Client
- 9 NIS Slave Servers
- 10 Changing Your NIS Passwords
- 11 Considerations For A Non NFS Environment
- 12 NIS Troubleshooting
- 13 Conclusion
Knoppix und keine Internetverbindung
Source
"La combinación de direcciones IP y máscaras de subred no es válida"
cuando cambio de ip en conexión de área local pongo una ip que es 192.168.0.175 mascara de red 255.255.255.240.
me sale este mensaje:
"La combinación de direcciones IP y máscaras de subred no es válida. Todos los bits en la porción dirección de host de la dirección ip están establecidos a 1. Escriba una combinación válida de direcciones IP y máscara de subred"
igual si le cambio el último rango de ip a .143, .144, .176 y otros por ahi.
Source
11.1 Automatische Konfiguration
Wenn sich unterstützte Netzwerkhardware in deinem PC befindet, so versucht Knoppix, diese während des Bootvorgangs zu konfigurieren und in das bestehende Netzwerk zu integrieren. Das funktioniert vollautomatisch, wenn sich in dem Netzwerk ein so genannter DHCP-Server befindet: Dieser weist der Netzwerkkarte automatisch eine Netzwerkadresse (eine sog. IP-Adresse) zu. Wenn du prüfen möchtest, ob dies in deinem Netz der Fall ist, so gehe folgendermaßen vor:

Hier klicken, um das Bild zu Vergrößern
Um die obige Verbindung zu testen, sollte dir die Adresse mindestens eines weiteren Rechners im lokalen Netz bekannt sein (z. B.: 192.168.0.103). Die Überprüfung der Netzwerkanbindung erfolgt mit Hilfe des Befehls ping. Sollte der DHCP-Server ein Router sein, der ebenfalls die Verbindung des Netzes zum Internet sicherstellt und als Gateway agiert, so kann schließlich auch noch versucht werden, einen Rechner im Internet anzupingen.

Hier klicken, um das Bild zu Vergrößern
11.2 Manuelle KonfigurationNicht jeder verfügt über einen Switch oder Router im LAN, welcher als DHCP-Server agiert. In diesem Fall muss man den Netzwerkzugang manuell konfigurieren. Unter Knoppix existieren für derartige Belange vielfältige Konfigurationsskripte. Den Netzwerkzugang konfiguriert man folgendermaßen per Hand:

Hier klicken, um das Bild zu Vergrößern

Hier klicken, um das Bild zu Vergrößern
Source
Mit plog sehe das ich im netz bin aber keine website ansurfen kann auch kein ftp oder icq
woran kann das liegen?
Das kann daran liegen, daß du das Gateway mitkonfigurierst.
Konfiguriere deine Netzwerkkarte in etwa so:
more /etc/network/interfaces
# /etc/network/interfaces -- configuration file for ifup, ifdown
# The loopback interface
# automatically added when upgrading
auto lo eth0
iface lo inet loopback
iface eth0 inet static
address 192.168.2.2
netmask 255.255.255.0
#network 192.168.2.0
#broadcast 192.168.2.255
#gateway 192.168.2.1
# network, broadcast, gateway auskommentiert (gateway via pon konfigurieren)
===========
Source
- "Intel? PRO/100 M Network Connection" auf dem Mainboard
ich habe es schon manchmal erlebt, dass Onboard-Netzwerkkarten
unter Knoppix nicht funktionierten, obwohl sie beim Booten z.B. als
eth0 erkannt wurden. :-(
- eth0... is broadcasting... (backrounding)
-----------------------
NIC manuell aufzusetzen:
"La combinación de direcciones IP y máscaras de subred no es válida"
cuando cambio de ip en conexión de área local pongo una ip que es 192.168.0.175 mascara de red 255.255.255.240.
me sale este mensaje:
"La combinación de direcciones IP y máscaras de subred no es válida. Todos los bits en la porción dirección de host de la dirección ip están establecidos a 1. Escriba una combinación válida de direcciones IP y máscara de subred"
igual si le cambio el último rango de ip a .143, .144, .176 y otros por ahi.
Source
11.1 Automatische Konfiguration

Wenn sich unterstützte Netzwerkhardware in deinem PC befindet, so versucht Knoppix, diese während des Bootvorgangs zu konfigurieren und in das bestehende Netzwerk zu integrieren. Das funktioniert vollautomatisch, wenn sich in dem Netzwerk ein so genannter DHCP-Server befindet: Dieser weist der Netzwerkkarte automatisch eine Netzwerkadresse (eine sog. IP-Adresse) zu. Wenn du prüfen möchtest, ob dies in deinem Netz der Fall ist, so gehe folgendermaßen vor:
| 1. | Öffne durch Anklicken des Konsolensymbols (das ist das bildschirmartige Icon im Panel) eine Shell und gib den folgenden Befehl ein: |
ifconfig
| 2. | Darauf sollten in etwa die folgenden Meldungen auf deinem Bildschirm erscheinen: |

Hier klicken, um das Bild zu Vergrößern
Abbildung 11.1 Automatische Konfiguration der Netzwerkkarte
Die obigen Informationen besagen folgendes: Dem ersten Netzwerkinterface (eth0) wurde die Internet Protokoll (IP) Adresse 192.168.0.1 zugeteilt. Wenn du eine entsprechende Nummer bei dir nach Eingabe von ifconfig vorfindest, so ist davon auszugehen dass die Karte einsatzbereit ist.Um die obige Verbindung zu testen, sollte dir die Adresse mindestens eines weiteren Rechners im lokalen Netz bekannt sein (z. B.: 192.168.0.103). Die Überprüfung der Netzwerkanbindung erfolgt mit Hilfe des Befehls ping. Sollte der DHCP-Server ein Router sein, der ebenfalls die Verbindung des Netzes zum Internet sicherstellt und als Gateway agiert, so kann schließlich auch noch versucht werden, einen Rechner im Internet anzupingen.

Hier klicken, um das Bild zu Vergrößern
Abbildung 11.2 Test der Verbindung ins LAN bzw. Internet mit ping
Der Ping-Prozess kann schließlich mit der Tastenkombination Strg + C wieder gestoppt werden. Sollte keine Verbindung zu Stande kommen, so ist der Netzwerkzugang manuell einzurichten:11.2 Manuelle KonfigurationNicht jeder verfügt über einen Switch oder Router im LAN, welcher als DHCP-Server agiert. In diesem Fall muss man den Netzwerkzugang manuell konfigurieren. Unter Knoppix existieren für derartige Belange vielfältige Konfigurationsskripte. Den Netzwerkzugang konfiguriert man folgendermaßen per Hand:
| 1. | Klicke auf das Knoppix-Menü-Symbol in der linken Häfte des Panels (das ist der kleine, stilisierte Pinguin). Wähle hier den Punkt Netzwerk/Internet -> Netzwerkkarte konfigurieren. |

Hier klicken, um das Bild zu Vergrößern
Abbildung 11.3 Konfiguration der Netzwerkschnittstelle
| 2. | Im ersten Schritt wirst du gefragt, ob ein DHCP-Broadcast zur Konfiguration der IP-Adresse verwendet werden soll. Diese Frage ist zur verneinen. |

Hier klicken, um das Bild zu Vergrößern
Abbildung 11.4 Manuelle Konfiguration der Netzwerkschnittstelle
| 3. | Danach wird eine IP-Adresse für das Netzwerkdevice abgefragt. Hier ist eine freie Adresse im Netz zu wählen. Wer lediglich den vorliegenden Computer verwenden möchte, benutzt am besten den vorgegebenen Standardwert (192.168.0.1). Die Netzwerkmasse ist ggf. anzupassen, meistens kann aber auch hier der vorgegebene Wert (255.255.255.0) übernommen werden. Das gleiche gilt für die im folgenden Dialog abgefragte Broadcastadresse. |
| 4. | Wer über einen Router verfügt, der als Internetgateway fungiert, gibt im nun folgenden Dialog dessen IP als Default-Gateway an. Der hier von Knoppix voreingestellte Wert (192.168.0.254) ist ggf. zu löschen, wenn kein Gateway existiert. |
| 5. | Als Nameserver kann entweder die Adresse des Gateways angegeben werden oder die Vorgabe (192.168.0.254) ggf. gelöscht werden. Moderne Router, die als DSL-Bridge arbeiten, geben zumeist die dynamisch vom Provider zugewiesene IP an das Netz weiter. |
| 6. | Schließlich wird der Konfigurationsdialog abgeschlossen, und die Netzwerkschnittstelle kann wie oben beschrieben getestet werden. |
FAQ (Frequently asked questions)
| Nach Eingabe des Befehls ifconfig erscheint bei mir keine eth0-Schnittstelle. Woran kann das liegen? |
Überprüfe zunächst die Netzwerkkabel. Sollte sich in deinem Netz ein DHCP-Server befinden, dann prüfe, ob dieser auch funktionsfähig ist. Ist das der Fall, so kann das Netzwerkmodul von Knoppix durch die Eingabe der folgenden Befehle in einer root-Konsole (Knoppix-Menü -> Root Shell) neu gestartet werden:
/etc/init.d/networking restart
pump -i eth0
Anschließend sollte die Netzwerkschnittstelle erneut mit dem Knoppix-Skript konfiguriert werden.===========================
Source
Mit plog sehe das ich im netz bin aber keine website ansurfen kann auch kein ftp oder icq
woran kann das liegen?
Das kann daran liegen, daß du das Gateway mitkonfigurierst.
Konfiguriere deine Netzwerkkarte in etwa so:
more /etc/network/interfaces
# /etc/network/interfaces -- configuration file for ifup, ifdown
# The loopback interface
# automatically added when upgrading
auto lo eth0
iface lo inet loopback
iface eth0 inet static
address 192.168.2.2
netmask 255.255.255.0
#network 192.168.2.0
#broadcast 192.168.2.255
#gateway 192.168.2.1
# network, broadcast, gateway auskommentiert (gateway via pon konfigurieren)
===========
Source
- "Intel? PRO/100 M Network Connection" auf dem Mainboard
ich habe es schon manchmal erlebt, dass Onboard-Netzwerkkarten
unter Knoppix nicht funktionierten, obwohl sie beim Booten z.B. als
eth0 erkannt wurden. :-(
- eth0... is broadcasting... (backrounding)
-----------------------
NIC manuell aufzusetzen:
ifconfig eth0 200.87.229.20 broadcast 192.168.0.255 netmask 255.255.255.252 up Dann:
Wildcard Masks
Source
This section looks at IP addressing, subnet masking, Private and Special addresses. Examples are provided to illustrate the methodology when setting up an IP network addressing scheme. We also look at Wildcard masks and Directed Broadcasts.
Wildcard MasksYou will often come across Wildcard masks, particularly if you work with OSPF and/or Cisco routers. The use of wildcard masks is most prevalent when building Access Control Lists (ACLs) on Cisco routers. ACLs are filters and make use of wildcard masks to define the scope of the address filter. Although ACL wildcard masks are used with other protocols, we will concentrate on IP here.
Let us first take a simple example. We may want to filter a sub-network 10.1.1.0 which has a Class C mask (24-bit) 255.255.255.0. The ACL will require the scope of the addresses to be defined by a wildcard mask which, in this example is 0.0.0.255. This means that the 'Don't care bits' are represented by binary 1's whilst the 'Do care bits' are represented by binary 0's. You will note that this is the exact opposite to subnet masks!
Taking a more complex example. Say we wish to filter out a subnet which is given by 10.1.1.32 having a mask of 255.255.255.224 i.e. 10.1.1.32/27. How do we find the wildcard mask for this? Well to help us, concentrating on the 4th octet, let us first look at the binary for this network and subnet mask. Then we reverse the binary bits to get the wildcard bits and then convert back to decimal to obtain the wildcard mask for the 4th octet:
| 4th octet in decimal | 32 |
|---|---|
| 4th octet in binary | 0 0 1 0 0 0 0 0 |
| 4th octet mask in decimal | 224 |
| 4th octet mask in binary | 1 1 1 0 0 0 0 0 |
| Now the 4th octet wildcard in binary | 0 0 0 1 1 1 1 1 |
| Now the 4th octet wildcard in decimal | 31 |
The important bits have been highlighted in bold and this shows that the wildcard mask for the network 10.1.1.32/27 is 0.0.0.31.
The following table should help in seeing a pattern between the number of bits used for the mask in a particular octet, the subnet mask in decimal and the equivalent wildcard mask:
| No. of Network Bits Set to 1 | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|---|
| Subnet Mask Binary | 0000 0000 | 1000 0000 | 1100 0000 | 1110 0000 | 1111 0000 | 1111 1000 | 11111100 | 1111 1110 | 11111111 |
| Subnet Mask Decimal | 0 | 128 | 192 | 224 | 240 | 248 | 252 | 254 | 255 |
| Wildcard Mask Binary | 1111 1111 | 0111 1111 | 0011 1111 | 0001 1111 | 0000 1111 | 0000 0111 | 00000011 | 0000 0001 | 00000000 |
| Wildcard Mask | 255 | 127 | 63 | 31 | 15 | 7 | 3 | 1 | 0 |
The binary for the wildcard mask is the exact reverse, bit for bit, of the subnet mask. You then calculate the decimal from the reversed binary bits to obtain the dotted decimal wildcard mask.
Private Addresses
One of the ways to combat the fast reduction in available IP address space was to introduce the concept of private addresses and the use of Network Address Translator (NAT) to allow many organisations to use the same address space but not have this space visible on the Internet i.e. to use address translation on the edge of the networks.
The Class A network address range 10.0.0.0 to 10.255.255.255 (10.0.0.0/8) is designated for private use only. This address range cannot be used on the Internet as every ISP will automatically drop the address. This address is becoming very popular as its use in conjunction with Network Address Translation (NAT) has meant that large corporations can make use of the Class A address space available within 10.0.0.0 for their own private use internally and just use NAT for those relatively few addresses that do need to operate on the Internet. This is one reason why the immediate need for IP version 6 has been diminished.
There is also the private address range 172.16.0.0 to 172.31.255.255 (172.16.0.0/12) which is the CIDR block of 16 x Class B addresses 172.16.0.0, 172.17.0.0, .... ,172.31.0.0.
The network address range 192.168.0.0 to 192.168.255.255 (192.168.0.0/16) is also for private use and is a CIDR block of 256 x Class C addresses 192.168.0.0, 192.168.1.0, .... ,192.168.255.0.
Examine RFC 1918 for more information on address allocation for private networks.
Other Special addresses
The address range 0.0.0.0/8 is currently considered throughout the Internet as for special use. Note that this is different from the host address 0.0.0.0/32 which means 'default'. You can have legitimate addresses in the range 0.0.0.0/16, e.g. 0.0.123.95/16.
The address range 192.0.2.0/24 is called the Test Net and is reserved for use in testing examples and documentation.
The address range 169.254.0.0/16 is used for auto-configuration of IP addresses if a DHCP server should fail and there is no backup for the DHCP Clients. This is described in RFC 2563 Stateless Auto-configuration.
Directed Broadcasts
The RFC 1812 overviews the requirements of routers to run IPv4. One of the requirements is that routers MUST, by default accept Directed Broadcasts (although it is allowable to have a switch that turns this off). A directed broadcast is one where the IP broadcast has been sent to a destination prefix (a net or subnet). A directed broadcast destined for the network 10.20.20.0/24 would be 10.20.20.255, for example.
Masking IP Addresses See Masking IP Address for information on hiding IP addresses.
Subnets
Source
This section looks at IP addressing, subnet masking, Private and Special addresses. Examples are provided to illustrate the methodology when setting up an IP network addressing scheme. We also look at Wildcard masks and Directed Broadcasts.
Subnets
Subnetting Example
Another Subnetting Example
Subnets
Subnetting Example
A customer has been given an IP address of 128.100.0.0 (a Class B address) for his company. He has specified that he requires 3 separate networks with the maximum possible number of host connections on each network.
The first two octets 128.100 are fixed since these are given by NIC as the Class B address, therefore we have the last two octets to play with. Let us examine the possibilities more closely:
- The address given
Octet 1 Octet 2 Octet 3 Octet 4 10000000 01100100 00000000 00000000 128. 100. 0. 0
- We need to create a minimum of 3 different subnets but not at the expense of the number of host addresses available to us. The following process would seem to give us 4 permutations of subnets: Looking at octet 3 specifically in binary, let us just use the first 2 bits for a subnet address:
128 64 32 16 8 4 2 1 1 1 0 0 0 0 0 0
The possible combinations for the first two bits are:11 = 192 -> 128.100.192.0 10 = 128 -> 128.100.128.0 01 = 64 -> 128.100.64.0 00 = 0 -> 128.100.0.0
However all 1's and all 0's used to be not allowed for a subnet. These subnets are called the All One's Subnet and Subnet Zero. The reason for this was that older software found it difficult to distinguish between networks 128.100.0.0/16 and the all-zeros subnet 128.100.0.0/18. The same was true of the all-ones subnet. RFC 950 therefore rules out '11' and '00' as useable subnets, we are therefore left with only two subnet addresses instead of the 3 we require.
- Let us try and use an extra bit in octet 3:
128 64 32 16 8 4 2 1 1 1 1 0 0 0 0 0
The possible combinations are now:111 = 224 -> 128.100.224.0 110 = 192 -> 128.100.192.0 101 = 160 -> 128.100.160.0 011 = 96 -> 128.100.96.0 001 = 32 -> 128.100.32.0 010 = 64 -> 128.100.64.0 100 = 128 -> 128.100.128.0 000 = 0 -> 128.100.0.0
As before all 1's and all 0's are not permitted for subnets, therefore we are left with 6 possible subnets (23 - 2):-128.100.32.0 128.100.64.0 128.100.96.0 128.100.128.0 128.100.160.0 128.100.192.0
- This leaves the rest of the bits (from power 16 downwards) in octet 3 and all the bits in octet 4 to construct the individual host addresses, the permutations amount to many thousands of hosts which should be plenty. Below is an example of a host address in subnet 128.100.192.0:-
128.100.194.23
On first inspection it would appear that address 128.100.194.23 has nothing to do with the subnet 128.100.192.0, so let us look a little more closely at the final two octets of the host address:Octet 3 = 194 Octet 4 = 23 128 64 32 16 8 4 2 1 128 64 32 16 8 4 2 1 1 1 0 0 0 0 1 0 0 0 0 1 0 1 1 1
As we can see we are indeed part of the 128.100.192.0 subnet since it is only the first three bits of octet 3 which are used for the subnet address. All the bits from power 16 and downwards are allocated to the host address, so the power 2 bit just turns octet 3 from decimal 192 to decimal 194. Confusion frequently arises in this situation where the dividing line between the network portion of the IP address and the host portion rests part way through an octet (in this case between power 32 and power 16 of octet 3). Often it is possible to make the network/host dividing line between octets so that you can easily tell which host address belongs to which subnet.Routers are used to minimise unnecessary traffic, and when running IP it is important to tell it which subnet an address is supposed to go. The way this is done, is at configuration by entering a 'subnet mask'.
The situation with the All-zeros and All-ones subnets nowadays is to allow them according to RFC 1878. This is because modern applications understand how to distinguish between these subnets and the main network.
Subnet masks The subnet mask specifies the portion of the IP address that is going to be used for subnetworks (as opposed to hosts). For every bit position in the IP address that is part of the network ID or subnetwork ID, a '1' is set, and for every bit position in the IP address that is part of the host id portion, a '0' is set. The router uses the boolean AND operation with an incoming IP address to 'lose' the host portion of the IP address i.e. the bits that are '0', and match the network portion with its routing table. From this, the router can determine out of which interface to send the datagram. This means that the 'Don't care bits' are represented by binary 0's whilst the 'Do care bits' are represented by binary 1's.
For our example above, because we used the first three bits in octet 3 for our subnet addressing the subnet mask would be:
Octet 1 Octet 2 Octet 3 Octet 4 11111111 11111111 11100000 00000000 255. 255. 224. 0
What is important is that the same mask is applied throughout the physical networks that share the same subnet part of the IP address. All devices connected to the networks that compose the subnet must have the same mask.
A Broadcast Address for a subnet is when all 1's are used in the host portion of the IP address. For example, for the IP address 10.17.20.4 and a mask of 255.255.255.0 the subnet is 10.17.20.0 and the host id is 4. The broadcast address within the 10.17.20.0 subnet is when the host id portion of the address is made up of all binary 1's. In this example the host portion is the last octet and if these 8 bits are set to 1 we have a broadcast address of 10.17.20.255. You can ping this, send messages to this and so on, a single line to server a multitude of end stations.
Often you will see the network mask represented as a number of bits e.g. for the above example address of 10.17.20.4 with a mask of 255.255.255.0, this can also be represented as 10.17.20.4/24, where the 24 represents 24 bits (3 octets) set to 1.
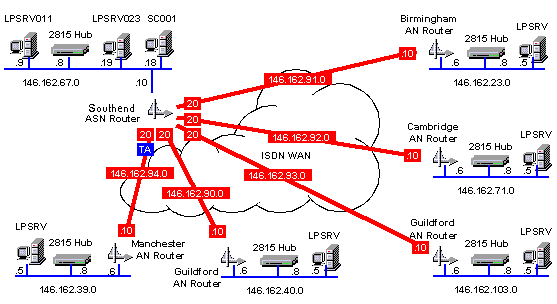
Study the schematic below: Another Subnetting Example

The network drawing above shows the IP address map for a WAN installation carried out for a large financial institution. The customer had installed 'Windows NT' servers at a number of sites and was requiring an ISDN link, star-wired out, from each of the sites from the main office server room. The IP addressing scheme had to take into account the following factors:-
- Up to 30 more sites may be added to the WAN in the near future.
- Each site could have up to 50 host connections.
- The customer had already assigned IP addresses to some of the servers and site PC's on the local LAN's.
The IP address given to this company was 146.162.0.0 (which is a Class B address), and the decision was made to use the whole of octet 3 for the subnet addresses leaving octet 4 for the host addresses. This made assigning IP addresses more easy to carry out and gave a maximum of 254 hosts per subnet and there could be a maximum of 254 subnets, thus satisfying the customer's requirements. The subnet mask for each subnet (Whether LAN or WAN) was consequently 255.255.255.0, it is important to design the addressing scheme such that the subnet mask is common to all LAN's/WAN's throughout the network unless a routing protocol such as OSPF is to be used. OSPF allows variable subnet masking.
Whilst studying the schematic you will note that the WAN links are 146.162.90.0 to 146.162.94.0 and the router ISDN interfaces are .20 at the main office end and .10 at the remote office end. Also you will note that the server IP addresses are all .5 and the ethernet hubs are all .8 while the router ethernet interfaces are all .6. Organising addressing like this can make life much easier especially when you are hopping from site to site.
RFC 950 and RFC 1812 describes IP subnetting whereas RFC 1009 defines Variable Length Subnet Masking.
Quick tricks to find subnets and broadcast addresses If you have a subnet mask, then it is possible to quickly list out the possible subnets and broadcast addresses.
The number by which subnets increment for a given mask is calculated by subtracting the last numbered octet in decimal from 256. For example, given the subnet 10.1.0.0 255.255.248.0, the last numbered octet is 248, therefore 256 - 248 = 8, so subnets jump up in 8's i.e. 10.1.8.0, 10.1.16.0, 10.1.24.0 etc.
Once you have found out by how much subnets jump, finding a broadcast address for each subnet is quickly done by subtracting 1 from this and adding this to each subnet. Using the above example, for subnet 10.1.8.0, the subnets jump in 8's, 8 - 1 = 7 and 8 + 7 = 15 so, taking it as given that the final octet will be all one's for the broadcast, the broadcast address is 10.1.15.255.
IP Address Classes
Source
This section looks at IP addressing, subnet masking, Private and Special addresses. Examples are provided to illustrate the methodology when setting up an IP network addressing scheme. We also look at Wildcard masks and Directed Broadcasts.
IP Address Classes Unique IP (Internet Protocol) addresses are assigned to each physical connection of a device to a network, therefore if a device (host) has more than one connection to a network or networks, then it will have more than one IP address.
An IP address is represented as four decimal integers, with each integer corresponding to one byte this means an IP address is 32 bits long as per the following example:-
162. 146. 93. 14 dotted decimal 10100010. 10010010. 01011101. 00001110 binary
IP addresses are divided into two parts, a Network ID and a Host ID each of which can be of varying bit lengths but always making 32 bits altogether.
Hint:- Use the Windows calculator to convert binary to decimal and vice versa.
There are five primary classes of IP addresses and it is the high order 3 bits of the address which identify the class as shown below:-
First Octet Example Network Host Class A 0xxxxxxx 1-127 25.234.45.0 1 Class B 10xxxxxx 128-191 140.250.43.0 1 Class C 110xxxxx 192-223 192.2.3.0 1 Class D 1110xxxx 224-239 232.56.4.0 1 Class E 11110000 240-254 242.5.7.0 1
Class A addresses contain 7 bits in the network portion giving 27 - 2 = 126 possible networks since all 1's and all 0's are not allowed. Consequently 24 bits remain for the host portion allowing a total of 224 - 2 = 16,777,214 hosts. 127.0.0.0/8 is reserved for loopback address purposes where just 127.0.0.1 is used normally. The address 255.255.255.255 is used as broadcast addresses and 0.0.0.0 as a default route address, meaning any network. The address 0.0.0.0 is sometimes used by hosts that have yet to receive an IP address e.g. a DHCP Client awaiting an address from the DHCP server.
Class B addresses contain 14 bits in the network portion allowing 214 - 2 = 16,384 possible networks, and 16 bits for the host portion allowing a possible total number of 216 - 2 = 65,534 hosts.
Class C addresses contain 21 bits for the network portion giving a possible total of 221 - 2 = 2,097,152 networks, and 8 bits for the host portion giving a possible 28 - 2 = 254 hosts.
Class D addresses are used for multicasting and Class E addresses are used in research.
Historically, a company may have been allocated just one Class A, B or C IP address by the Network Information Centre (NIC). Currently, all Class A addresses have been allocated and most if not all of the Class B addresses have gone. If a company have a number of networks to manage then the network administrator may wish to subnet his network, that is create subnet addresses within the scope of the IP address that the administrator has been given.
Workgroup Ubuntu - Windows
Source
Windows 7 uses a feature called homegroup, which enhances the workgroup feature in order to make home networking easier for all Windows 7 computers. However, this feature doesn't work on Linux or older version of Windows. In order to connect your Linux computers to Windows 7 computers and share files and folders, you need to make a series of settings. First, it is to change the workgroup, so that all computers belong to one workgroup. In this tutorial I will demonstrate how to configure and change the workgroup on an Ubuntu PC.
Step 1: Install Samba 


Step 2: Configure the Samba Workgroup 



How to Access Windows 7 Shared Folders from Ubuntu
How to Access Ubuntu Shared Folders from Windows 7
Accessing Shared Partitions from Ubuntu & Windows 7
How to Change the Workgroup in Windows 7
How to Customize Network Sharing Settings in Windows 7
Share Libraries or Folders Using the Sharing Wizard
Windows 7 uses a feature called homegroup, which enhances the workgroup feature in order to make home networking easier for all Windows 7 computers. However, this feature doesn't work on Linux or older version of Windows. In order to connect your Linux computers to Windows 7 computers and share files and folders, you need to make a series of settings. First, it is to change the workgroup, so that all computers belong to one workgroup. In this tutorial I will demonstrate how to configure and change the workgroup on an Ubuntu PC.
Step 1: Install Samba
Samba is a package for Unix systems that provides support for cross-platform files and printers sharing, and is needed for Ubuntu to access shared resources on a Windows network. In this case, you'll need to add your Ubuntu PC to a workgroup in order to connect to a Windows network. To install Samba, access your Terminal application from your main panel in 'Applications - Accessories - Terminal'.
In your terminal, you'll need to install the "samba" and "smbfs" packages, by typing the following command:
sudo apt-get install samba smbfs
You may be asked for your administrator password, which will be the same password that you use to log into your PC. After typing it in, hit Y to confirm the installation.

When the installation finishes, you will be returned to the command line prompt.

Step 2: Configure the Samba Workgroup
Still in your terminal, open the Samba configuration file by using this command:
sudo gedit /etc/samba/smb.conf
In this file, find the workgroup setting and change the value to match the workgroup of your Windows 7 PC.

You need to save the file, by clicking the Save (disk) icon near the top of the window.

Now, restart Samba using the following command:
sudo service samba restartor sudo service smbd restart

This will add your Ubuntu PC to the same workgroup as your Windows 7 computers. This will allow you to share files, folders, and printers between computers. Once your PC is part of the workgroup, it will show up in your list of workgroup computers, and allow you to see other computers already added to it.
Conclusion
You can configure an Ubuntu (or any Linux PC) to join a Windows workgroup in order to be visible on the same network and share files, folders, and printers. If you want to know more about setting up other PC's on a local network, or how to further utilize the networking features between Linux and Windows 7, check out the articles listed below.
Related articles:How to Access Windows 7 Shared Folders from Ubuntu
How to Access Ubuntu Shared Folders from Windows 7
Accessing Shared Partitions from Ubuntu & Windows 7
How to Change the Workgroup in Windows 7
How to Customize Network Sharing Settings in Windows 7
Share Libraries or Folders Using the Sharing Wizard
Browser Defender
cant-uninstall-browser-defender-and-spyware
Browser Defender is a plugin. You can manage your plugins via support, my account. When it is a plugin, it runs silently with IE.
It runs as a service to update as necessary. I would leave it alone unless you want to uninstall it. It takes little resources and I would recommend to keep it.
If you decide to uninstall it, you do so via add/remove programs. It will not affect SD per se. It will reduce the IE protection against bad web sites.
Buscar en complementos de firefox, si se quiere deactivarlo
Browser Defender by ThreatExpert, a SiteAdvisor Alternative
Browser Defender is a plugin. You can manage your plugins via support, my account. When it is a plugin, it runs silently with IE.
It runs as a service to update as necessary. I would leave it alone unless you want to uninstall it. It takes little resources and I would recommend to keep it.
If you decide to uninstall it, you do so via add/remove programs. It will not affect SD per se. It will reduce the IE protection against bad web sites.
Buscar en complementos de firefox, si se quiere deactivarlo
Browser Defender by ThreatExpert, a SiteAdvisor Alternative
Update Flash Player on Windows Vista and Windows 7
Source
On some Windows Vista and Windows 7 systems, Flash Player is installed, but does not display Flash content.
If the installed Flash Player is between version 9.0.28.0 to 10.0.45.0, use a special installation utility that uninstalls Flash Player and then installs the latest Flash Player. This utility is for Flash Player for Internet Explorer. Follow these steps:
The Flash Player 10.1 uninstall utility in the Macromed\Flash folder has the following names:
Both of these utilities uninstall Flash Player for Internet Explorer and Flash Player for other browsers such as Firefox. If you want to uninstall Flash Player for Internet Explorer only, use the Windows Control Panel to remove the program Adobe Flash Player 10 ActiveX. To uninstall Flash Player only for other browsers, remove the program Adobe Flash Player 10 Plugin.
For more information about the utilities in the Macromed\Flash folder, see Installation issues when switching between release and debugger versions during development and testing (TechNote 4da116d3).

On some Windows Vista and Windows 7 systems, Flash Player is installed, but does not display Flash content.
If the installed Flash Player is between version 9.0.28.0 to 10.0.45.0, use a special installation utility that uninstalls Flash Player and then installs the latest Flash Player. This utility is for Flash Player for Internet Explorer. Follow these steps:
- Open Windows Explorer and navigate to one of the following folders (only one exists depending on your operating system):
- C:\Windows\System32\Macromed\Flash\
- C:\Windows\SysWOW64\Macromed\Flash\
- Locate the installation utility. It is a file with a name like FlashUtil10d.exe. The number and the letter, such as 10d in this example, depend on the installed Flash Player version.
- Close all applications except for Windows Explorer.
- Right-click the installation utility (FlashUtil10d.exe in this example).
- Select Run as administrator to execute the installer with administrator permissions.

- Select Yes in the User Account Control display, if it pops up.
- Select Install Now to install the update to Adobe Flash Player.

- Check the license agreement and select Install in the Install Adobe Flash Player display.

- When the install completes, select Done.
- Restart your computer.
The Flash Player 10.1 uninstall utility in the Macromed\Flash folder has the following names:
- FlashUtil10*_ActiveX.exe
- FlashUtil10*_Plugin.exe
Both of these utilities uninstall Flash Player for Internet Explorer and Flash Player for other browsers such as Firefox. If you want to uninstall Flash Player for Internet Explorer only, use the Windows Control Panel to remove the program Adobe Flash Player 10 ActiveX. To uninstall Flash Player only for other browsers, remove the program Adobe Flash Player 10 Plugin.
For more information about the utilities in the Macromed\Flash folder, see Installation issues when switching between release and debugger versions during development and testing (TechNote 4da116d3).
Bridging Ethernet Connections
Source
This covers how to bridge connections with Kubuntu 6.06 (Dapper) using the package bridge-utils. Bridging two ethernet connections is the focus of this article. It is assumed that the bridging computer is not directly connected to the internet. This article was created by way of paraphrasinghttp://linux-net.osdl.org/index.php/Bridge. Please visit this site if you need a more in-depth discussion of network bridges and the commands used here.
Additional information on monitoring network activity and setting up a bridge in Ubuntu 6.06 (Dapper) can be found at NetworkMonitoringBridge.
Specifically, this article has been written for Kubuntu 6.06 (Dapper), however, it should be available for use on any distribution of Linux and certainly Ubuntu 6.06 (Dapper) for that matter (you will need to know the Default Gateway IP Address, however, if you wish to use the internet on the bridging computer).
Please note that the bridge-utils package only works if you are using a Linux kernel 2.3 or higher.
The first step is to download bridge-utils. Ensure that you have all of the typical repositories loaded.
Installing bridge-utils
Adept
Search for bridge-utils and choose the drop-down arrow on the left. Choose "request install".
Konsole:
Enter this into Konsole:
sudo apt-get update sudo apt-get install bridge-utils
If you use sudo -i and enter your password, then you will not have to use sudo before each command. It may also save you some typing in the future.
Setting up the Bridge
Ensure that both (or all) of your interfaces are installed and enabled. If they are then you may proceed at this point. For a few moments, if your computer is connected to the internet then it will be disconnected until a certain point is reached.
Open Konsole and use the following commands. Note that when interfaces are referenced, they refer to device names assigned by linux such as "eth0" and "eth1". Also note that myBridge is the name of the bridge that you wish to have. This can be anything, but a simple name like bridge0 or bridge1 is suggested.
ifconfig0.0.0.0 < > ifconfig 0.0.0.0 < > brctl addbr < > brctl addif < > brctl addif < > ifconfig up
In lines 1-2 we simply prepared the devices to be bridged. In line 3, we added a new bridge named myBridge (whatever you named your bridge). In lines 4-5, we added interface1 and interface2 to myBridge. In line 6, we made the bridge operational. For more information on commands: use the Konsole command brctl
Create the Bridge at Start-up
The above setup demonstrated how to create a bridge using the command line, however when you restart your computer you will lose it. To prevent this from happening, we need to edit the /etc/network/interfaces file. This file shows an example of a bridge configure via dhcp.
Sample /etc/network/interfaces file
# This file describes the network interfaces available on your system # and how to activate them. For more information, see interfaces(5). # The loopback network interface auto lo iface lo inet loopback # Bridge between eth0 and eth1 auto br0 iface br0 inet dhcp # For static configuration delete or comment out the above line and uncomment the following: # iface br0 inet static # address 192.168.1.10 # netmask 255.255.255.0 # network 192.168.1.0 # gateway 192.168.1.1 # dns-nameservers 192.168.1.5 # dns-search example.com pre-up ifconfig eth0 down pre-up ifconfig eth1 down pre-up brctl addbr br0 pre-up brctl addif br0 eth0 pre-up brctl addif br0 eth1 pre-up ifconfig eth0 0.0.0.0 pre-up ifconfig eth1 0.0.0.0 post-down ifconfig eth0 down post-down ifconfig eth1 down post-down ifconfig br0 down post-down brctl delif br0 eth0 post-down brctl delif br0 eth1 post-down brctl delbr br0
Restart networking
sudo /etc/init.d/networking restart
Notes about the setup
You have successfully completed an invisible bridge between your interfaces. If computer doing the bridging's purpose is simply to act as a switch and nothing more, then you are done. However, most users will still want to be able access the internet (and the rest of the network for that matter from the computer). Please read below to see how to do this.
Enabling Internet Use on the Bridging Computer
It is very simple to setup the internet on the bridging computer.
Finding the Default Gateway
These directions below attempt to locate your default gateway. They are not foolproof and if you are not sure what your default gateway is then contact your Network Administrator or see the Kubuntu IRC channel if the Administrator is you. If you know your default gateway, then skip to the
1. If the internet worked on your computer before, then open the KDE Panel and choose system settings. 2. Open System Settings and next click Network Settings. 3. Click the "Administrator Mode..." button at the bottom of the window and enter your password. 4. Choose the "Route" tab and remember, write down, or copy the address inside the Default Gateway group box and the "IP Address" text box.
You now have your default gateway IP address. It is now possible to setup your computer to access the internet through the bridge.
Konsole Commands
Once you have your default gateway then enter these commands below.
route add default gatewaydhclient
If you get a message back from the first command, such as
SIOCADDRT: File exists
or
SIOCADDRT: Network is unreachable
Then skip to the second command.
To ensure that you are connected to the internet, ping the IP address with the command below.
To ensure that you are connected to the internet, ping the IP address with the command below.
ping 66.94.234.13
If you get in Konsole:
# ping 66.94.234.13 PING 66.94.234.13 (66.94.234.13) 56(84) bytes of data. 64 bytes from 66.94.234.13: icmp_seq=1 ttl=55 time=386 ms 64 bytes from 66.94.234.13: icmp_seq=2 ttl=55 time=250 ms 64 bytes from 66.94.234.13: icmp_seq=3 ttl=55 time=283 ms 64 bytes from 66.94.234.13: icmp_seq=4 ttl=55 time=256 ms 64 bytes from 66.94.234.13: icmp_seq=5 ttl=55 time=247 ms 64 bytes from 66.94.234.13: icmp_seq=6 ttl=55 time=254 ms
Then you are done! However, if you do not, double check your work by taking down the bridge:
ifconfigdown brctl delbr
And then go through the steps once more. Once again, you can get more help on the brctl command by typing brctl into Konsole.
At this point you may also want to see http://linux-net.osdl.org/index.php/Bridge at this point for a more in depth explanation of bridges and other commands within brctl.
Subscribe to:
Comments (Atom)




 LibreOffice
LibreOffice Firefox
Firefox